kubernetes快速入门12-dashboard
2021-01-02 02:27
标签:ace 加载 awl tcp describe ast ovf das dml 更多信息请参考:https://github.com/kubernetes/dashboard 此yaml应用后会创建一个名为 service是以ClusterIP方式工作,要想访问web界面需要在集群内使用 使用浏览器访问 提供了两种认证方式。 创建认证token的流程: 把此token复制粘贴到登陆界面就可登陆管理k8s集群。 基于上边创建的名为 现在就可把 这里创建的 这个token登陆dashboad就只能管理default名称空间的资源。 如果要想删除一个已创建的用户可以使用以下命令 kubernetes快速入门12-dashboard 标签:ace 加载 awl tcp describe ast ovf das dml 原文地址:https://blog.51cto.com/zhaochj/2533738安装
# 安装
k8s@node01:~$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.3/aio/deploy/recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper createdkubernetes-dashboard的名称空间,recommended.yaml中创建的资源都放在此名称空间中k8s@node01:~$ kubectl get pod -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-6b4884c9d5-74pmh 1/1 Running 0 9m13s
kubernetes-dashboard-7f99b75bf4-zgqbh 1/1 Running 0 9m13s
k8s@node01:~$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.102.153.202 集群IP地址访问,可以在master节点上做代理,也可以直接修改service,让其以NodePort方式工作k8s@node01:~$ kubectl patch svc kubernetes-dashboard -p ‘{"spec":{"type":"NodePort"}}‘ -n kubernetes-dashboard
k8s@node01:~$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.100.214.241 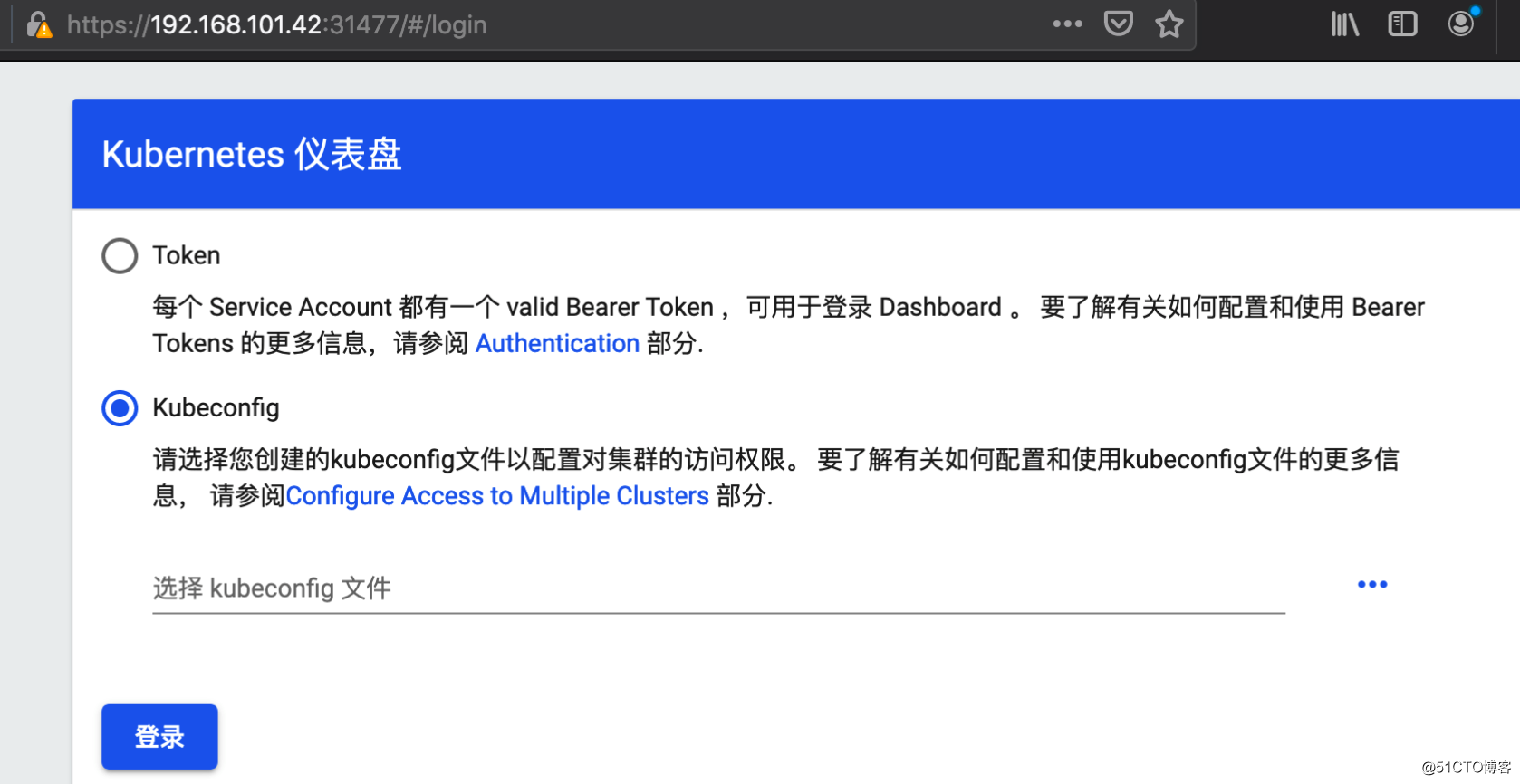
基于token认证
cluster-admin的clusterrole和名为cluster-admin的clusterrolebinding进行绑定# 创建serviceaccount用户
k8s@node01:~$ kubectl create serviceaccount dashboard-cluster-user -n kubernetes-dashboard
# 相对应的资产清单文件为
k8s@node01:~$ kubectl create serviceaccount dashboard-cluster-user -n kubernetes-dashboard -o yaml --dry-run=client
apiVersion: v1
kind: ServiceAccount
metadata:
creationTimestamp: null
name: dashboard-cluster-user
namespace: kubernetes-dashboard
k8s@node01:~$ kubectl get serviceaccount -n kubernetes-dashboard
NAME SECRETS AGE
dashboard-cluster-user 1 18m
default 1 67m
kubernetes-dashboard 1 67m
# 绑定角色
k8s@node01:~$ kubectl create clusterrolebinding dashboard-cluster-role-bind --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-cluster-user
# 相对应的资产清单文件为
k8s@node01:~$ kubectl create clusterrolebinding dashboard-cluster-role-bind --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-cluster-user -o yaml --dry-run=client
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: dashboard-cluster-role-bind
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-cluster-user
namespace: kubernetes-dashboard
k8s@node01:~$ kubectl get clusterrolebinding
NAME ROLE AGE
cluster-admin ClusterRole/cluster-admin 8d
dashboard-cluster-role-bind ClusterRole/cluster-admin 50s
...
# 授权后会自动生成相应的secret资源对象
k8s@node01:~$ kubectl get secret -n kubernetes-dashboard
NAME TYPE DATA AGE
dashboard-cluster-user-token-xvmh9 kubernetes.io/service-account-token 3 6m53s
...
# 获取token
k8s@node01:~$ kubectl describe secret dashboard-cluster-user-token-xvmh9 -n kubernetes-dashboard
Name: dashboard-cluster-user-token-xvmh9
Namespace: kubernetes-dashboard
Labels: 基于kubeconfig认证
dashboard-cluster-user的serviceaccount的用户,再让其可以使用kubeconfig方式登陆# 创建需要管理的集群
k8s@node01:~$ sudo kubectl config set-cluster kubernetes01 --server="https://192.168.101.40:6443" --certificate-authority=/etc/kubernetes/pki/ca.key --kubeconfig=/home/k8s/def-cluster-adm.conf
# token定义为一个变量,方便后边引用
k8s@node01:~$ TOKEN_TMP=eyJhbGciOiJSUzI1NiIsImtpZCI6Ino3XzB5Rk5FT1ROTmNTSi1ydVZiNWJ3aDlzckxndDk4bzd6dE81anRIVGsifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtY2x1c3Rlci11c2VyLXRva2VuLXh2bWg5Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImRhc2hib2FyZC1jbHVzdGVyLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2OGEwNmQ5NS1iMjAwLTRhN2YtOTUzYi1iZDUxMmE5OTYxZGMiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6ZGFzaGJvYXJkLWNsdXN0ZXItdXNlciJ9.SWdsI8spBeWLKiANxp1RNF_KAHD_Hfd913fKNpergi83jwO6ZwvVwXSg8INMvGDoqPFSPsPkW2_l8U2bEP65vqkcrQxTFnkaJ94z45oVfMiVLsbOq6RbOTi7uHsA1wBCXKk1c5yI3Mw8KpX30vKsGTvEL_FIsgm1M6bQ9X-X2MgiZr9PFR3cTwvwHBjmbQXD9oNbwIJwY2yJv87lnE6EvrKp_Nyf_l4BfPDBIn3cyiQA0WCj910yJN13UVtkP1mtwyWANASGF-BH3vkUHFtvLaxnMQsEUEQJZdFex_osyqNV06-JrR6lseXPRBK7GngVdUqDhRbX-ldSxfik-lizvA
# 使用token信息创建用户
k8s@node01:~$ sudo kubectl config --kubeconfig=/home/k8s/def-cluster-adm.conf set-credentials dashboard-cluster-user --token=$TOKEN_TMP
# 创建上下文
k8s@node01:~$ sudo kubectl config --kubeconfig=/home/k8s/def-cluster-adm.conf set-context dashboard-cluster-user@kubernetes01 --cluster=kubernetes01 --user=dashboard-cluster-user
# 设置当前使用的集群
k8s@node01:~$ sudo kubectl config --kubeconfig=/home/k8s/def-cluster-adm.conf use-context dashboard-cluster-user@kubernetes01
Switched to context "dashboard-cluster-user@kubernetes01".
# 查看配置文件
k8s@node01:~$ sudo cat def-cluster-adm.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority: /etc/kubernetes/pki/ca.key
server: https://192.168.101.40:6443
name: kubernetes01
contexts:
- context:
cluster: kubernetes01
user: dashboard-cluster-user
name: dashboard-cluster-user@kubernetes01
current-context: dashboard-cluster-user@kubernetes01
kind: Config
preferences: {}
users:
- name: dashboard-cluster-user
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6Ino3XzB5Rk5FT1ROTmNTSi1ydVZiNWJ3aDlzckxndDk4bzd6dE81anRIVGsifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtY2x1c3Rlci11c2VyLXRva2VuLXh2bWg5Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQubmFtZSI6ImRhc2hib2FyZC1jbHVzdGVyLXVzZXIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI2OGEwNmQ5NS1iMjAwLTRhN2YtOTUzYi1iZDUxMmE5OTYxZGMiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6a3ViZXJuZXRlcy1kYXNoYm9hcmQ6ZGFzaGJvYXJkLWNsdXN0ZXItdXNlciJ9.SWdsI8spBeWLKiANxp1RNF_KAHD_Hfd913fKNpergi83jwO6ZwvVwXSg8INMvGDoqPFSPsPkW2_l8U2bEP65vqkcrQxTFnkaJ94z45oVfMiVLsbOq6RbOTi7uHsA1wBCXKk1c5yI3Mw8KpX30vKsGTvEL_FIsgm1M6bQ9X-X2MgiZr9PFR3cTwvwHBjmbQXD9oNbwIJwY2yJv87lnE6EvrKp_Nyf_l4BfPDBIn3cyiQA0WCj910yJN13UVtkP1mtwyWANASGF-BH3vkUHFtvLaxnMQsEUEQJZdFex_osyqNV06-JrR6lseXPRBK7GngVdUqDhRbX-ldSxfik-lizvAdef-cluster-adm.conf文件复制到需要登陆dashboard界面的主机上选择使用Kubeconfig的方式加载该配置文件进行认证登陆。dashboard-cluster-user这个serviceaccount绑定的是名为cluster-admin这个clusterrole资源,是属于集群级别的管理,也就是登陆dashboard后进行的管理是针对整个集群的所有名称空间里的所有资源进行管理,权限是非常大的。如果想进行更加精细的管理,让用户只能对指定的名称空间里的资源进行管理,那在进行角色绑定时就不能绑定cluster-admin这个集群角色,而应该绑定一个名称为admin的角色,以下边操作为例子:# 创建一个serviceaccount,计划用户只能管理default名称空间里的资源
k8s@node01:~$ kubectl create serviceaccount def-default-adm -n default
# 使用rolebinding绑定角色
k8s@node01:~$ kubectl create rolebinding def-default-adm --clusterrole=admin --serviceaccount=default:def-default-adm
# 获取token
k8s@node01:~$ kubectl get secret
NAME TYPE DATA AGE
def-default-adm-token-kmgmd kubernetes.io/service-account-token 3 2m54s
default-token-ndclg kubernetes.io/service-account-token 3 9d
ingress-https kubernetes.io/tls 2 3d8h
mysa-token-fq592 kubernetes.io/service-account-token 3 27h
mysql-password Opaque 1 2d
k8s@node01:~$ kubectl describe secret def-default-adm-token-kmgmd
Name: def-default-adm-token-kmgmd
Namespace: default
Labels: $ sudo kubectl --kubeconfig=/home/k8s/def-cluster-adm.conf config unset users.用户名称