xxh亲测openstack的api操作
2020-12-19 00:34
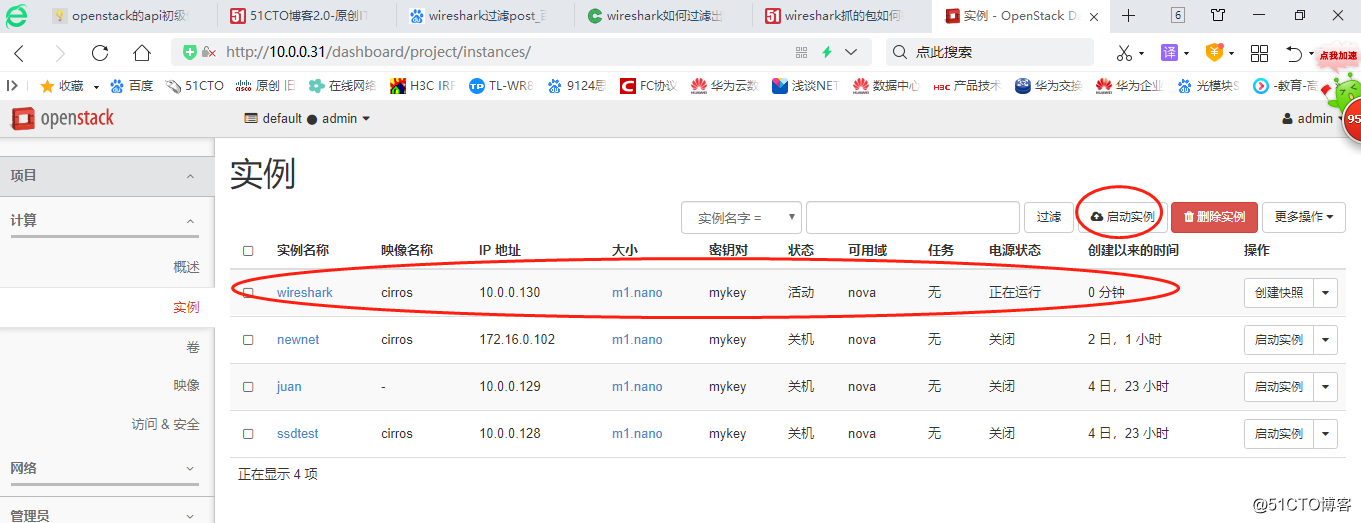
标签:image mamicode 老师 live 标识 wireshark def war ofo 2.web上新建名称为wireshark的实例 POST /v2.1/c0e784c602af4b40933a78bc3dcda542/servers HTTP/1.1 {"server": {"name": "wireshark", "imageRef": "4dea33ea-a34f-4e07-845a-4c212deee901", "availability_zone": "nova", "key_name": "mykey", "flavorRef": "0", "OS-DCF:diskConfig": "AUTO", "max_count": 1, "min_count": 1, "networks": [{"uuid": "a730ba59-ca28-48e6-a7f6-11703e879b30"}], "security_groups": [{"name": "04a70b53-eea2-4b45-a11a-d66624b2c612"}]}} 通过上面信息,构建一个api的url,用此url构建出第二台虚拟机wireshark2,我构造出来的api url如下: 案例二:抓包构造出删除云主机(实例)的url (2)删除主机抓包得到api DELETE /v2.1/c0e784c602af4b40933a78bc3dcda542/servers/e22e0fd1-44e2-487d-a37c-5d36c721ec1b HTTP/1.1 下面是我通过上面的包构建出来的! 备注:后面http是http://controller:8774/v2.1/c0e784c602af4b40933a78bc3dcda542/servers/[id] 案例三:抓包构造出删除卷、删除镜像等等操作的url都可以类似方法弄出来 明天再补充 (3) 删除一个卷抓包得到api (4)新建卷 xxh亲测openstack的api操作 标签:image mamicode 老师 live 标识 wireshark def war ofo 原文地址:https://blog.51cto.com/8189171/2546795
1.wireshark打开抓vmware vmnet8的网卡,过滤条件tcp.port == 8774 && http.request.method == POST 开始启动!
3.过滤条件tcp.port == 8774 && http.request.method == POST有数据了,打开此http流,图片如下: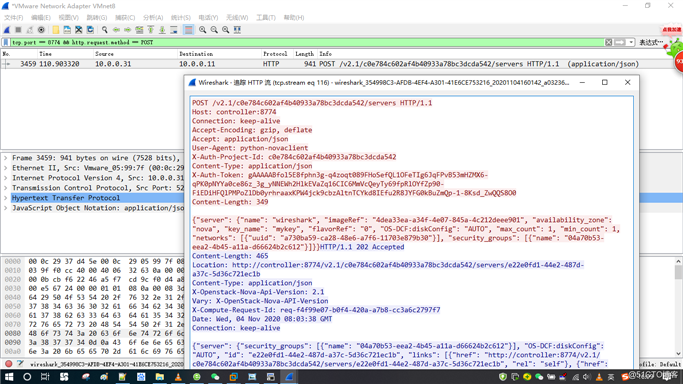
Host: controller:8774
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: application/json
User-Agent: python-novaclient
X-Auth-Project-Id: c0e784c602af4b40933a78bc3dcda542
Content-Type: application/json
X-Auth-Token: gAAAAABfol5E8fphn3g-q4zoqt089FHoSefQL1OFeTIg6JqFPvB53mHZMX6-qPK0pNYYa0ce86z_3g_yNNEWh2HlkEVaZq16CIC6MmVcQeyTy69fpRlOYfZp90-FiEDiHFQlPMPoZlDb0yrhraaxKPW4jck9cbzAltnTCYkd8IEfu2R8JYFG0kBuZmQp-1-8Ksd_ZwQQS8O0
Content-Length: 349
curl -X POST -H "Content-Type: application/json" -H "X-Auth-Token: gAAAAABfol5E8fphn3g-q4zoqt089FHoSefQL1OFeTIg6JqFPvB53mHZMX6-qPK0pNYYa0ce86z_3g_yNNEWh2HlkEVaZq16CIC6MmVcQeyTy69fpRlOYfZp90-FiEDiHFQlPMPoZlDb0yrhraaxKPW4jck9cbzAltnTCYkd8IEfu2R8JYFG0kBuZmQp-1-8Ksd_ZwQQS8O0" -d ‘
{
"server": {
"name": "wireshark2",
"imageRef": "4dea33ea-a34f-4e07-845a-4c212deee901",
"availability_zone": "nova",
"key_name": "mykey",
"flavorRef": "0",
"OS-DCF:diskConfig": "AUTO",
"max_count": 1,
"min_count": 1,
"networks": [{
"uuid": "a730ba59-ca28-48e6-a7f6-11703e879b30"
}],
"security_groups": [{
"name": "04a70b53-eea2-4b45-a11a-d66624b2c612"
}]
}
}‘ http://controller:8774/v2.1/c0e784c602af4b40933a78bc3dcda542/servers
之后也成功建立出来虚拟机了!(注意格式化的json串在cli执行前用文本工具吧tab替换为空格哈!)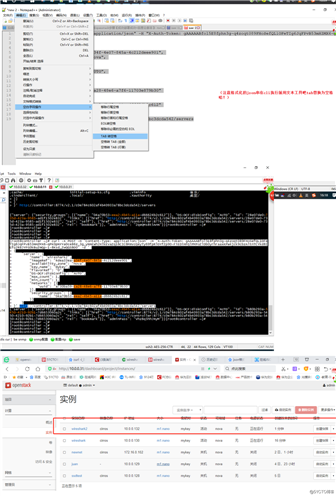
抓包过滤条件是tcp.port == 8774 && http.request.method == DELETE
得到抓包信息如下:
Host: controller:8774
Connection: keep-alive
Accept-Encoding: gzip, deflate
Accept: application/json
User-Agent: python-novaclient
X-Auth-Project-Id: c0e784c602af4b40933a78bc3dcda542
X-Auth-Token: gAAAAABfol5E8fphn3g-q4zoqt089FHoSefQL1OFeTIg6JqFPvB53mHZMX6-qPK0pNYYa0ce86z_3g_yNNEWh2HlkEVaZq16CIC6MmVcQeyTy69fpRlOYfZp90-FiEDiHFQlPMPoZlDb0yrhraaxKPW4jck9cbzAltnTCYkd8IEfu2R8JYFG0kBuZmQp-1-8Ksd_ZwQQS8O0
Content-Length: 0
准备删除wireshark4 他的标识是 c7a8e5bc-34d8-4373-a7b8-3b6f6de01aec
curl -X DELETE -H "Content-Type: application/json" -H "X-Auth-Token: gAAAAABfol5E8fphn3g-q4zoqt089FHoSefQL1OFeTIg6JqFPvB53mHZMX6-qPK0pNYYa0ce86z_3g_yNNEWh2HlkEVaZq16CIC6MmVcQeyTy69fpRlOYfZp90-FiEDiHFQlPMPoZlDb0yrhraaxKPW4jck9cbzAltnTCYkd8IEfu2R8JYFG0kBuZmQp-1-8Ksd_ZwQQS8O0" http://controller:8774/v2.1/c0e784c602af4b40933a78bc3dcda542/servers/c7a8e5bc-34d8-4373-a7b8-3b6f6de01aec
其中c0e784c602af4b40933a78bc3dcda542是admin项目的id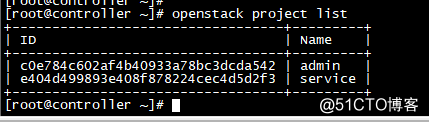
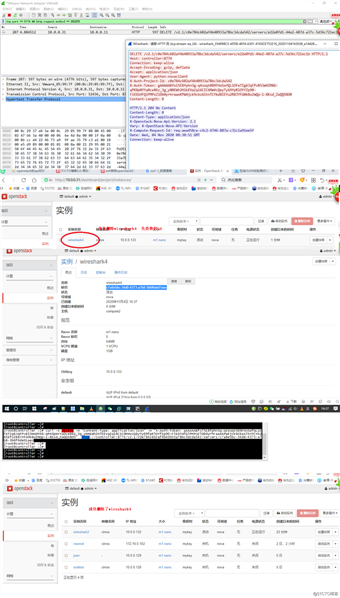
此外那个token也可以像老师那样先抓出来利用$token变量存储起来直接引用就不需要那么长一段书写了
tcp.port == 8776 && http.request.method == DELETE
tcp.port == 8776 && http.request.method == POST
文章标题:xxh亲测openstack的api操作
文章链接:http://soscw.com/index.php/essay/37209.html