SSL证书 - Let's Encrypt 证书部署 HTTPS
2021-01-02 05:28
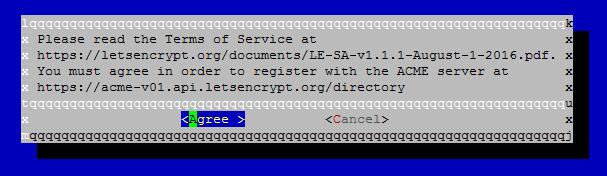
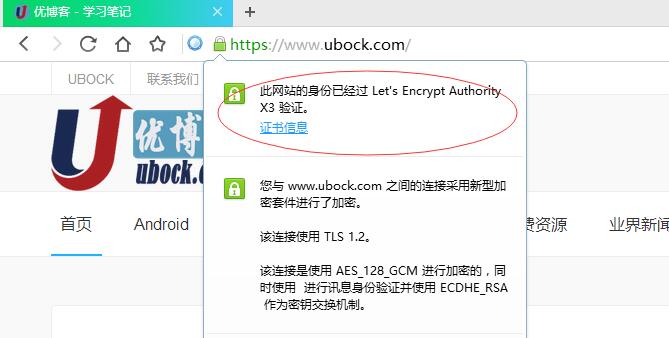
标签:tac https 打开网页 ble OWIN web服务 The 执行 chm 这里学习了ssl证书的安装,这里备份一下以免丢失。原文地址:https://ubock.com/article/25 系统: centOS 7.1 执行 /usr/share/nginx/html是网站根目录 上图片中输入邮箱,然后确认 上图片中直接Agree 如果出现下面的提示后一直卡住不动,可以重新执行一次,我就是重新执行后才行的 如果出现下面的提示,则需要修改nginx配置: 修改/etc/nginx/nginx.conf文件,在http的server中添加如下配置: 再重新执行获取证书命令 如果出现如下提示,恭喜你,成功了,证书有效期3个月,到时候后可以续期 在完成Let‘s Encrypt证书的生成之后,我们会在"/etc/letsencrypt/live/ubock.com/"域名目录下有4个文件就是生成的 密钥证书文件。 cert.pem - Apache服务器端证书 证书的路径最好不要移动,这样续期时就不需要再移动了 修改/etc/nginx/nginx.conf文件 修改好后保存退出 实现http强制重定向https 修改/etc/nginx/nginx.conf文件,在http的server最后增加如下配置: 注意不能添加在 前面,否则续期时可能会有问题 当证书成功获取后,用下面命令测试是否可以续期,此命令只是测试用,不会更新证书 当出现下面提示后,则测试成功,可以续期 输入: 回车,然后可以像使用vi编辑其他任何文件那样修改crontab文件 设置了每周一凌晨4点30自动更新证书,如果更新成功就自动重启nginx服务,证书在到期前30天内才能更新,多余的更新会自动忽略掉的,每周更新还有一个好处是更新可能会失败,这样最多还有4次的尝试机会来保证不会过期. SSL证书 - Let's Encrypt 证书部署 HTTPS 标签:tac https 打开网页 ble OWIN web服务 The 执行 chm 原文地址:https://www.cnblogs.com/rain-in-summer/p/13671632.html
Let‘s Encrypt是一个公共且免费SSL的项目,由Mozilla、Cisco、Akamai、IdenTrust、EFF等组织发起,主要的目的是为了推进网站从HTTP向HTTPS过度。我的部署环境
web服务器:Nginx 1.10.2
python 2.7安装 certbot
sudo yum install certbot获取证书
certbot certonly --webroot -w /usr/share/nginx/html -d ubock.com -d www.ubock.com
-d 后面是域名,多个域名就是写多个-d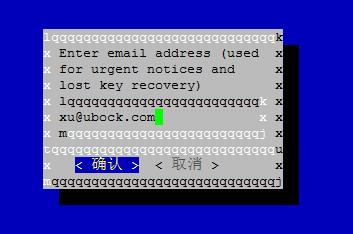
Starting new HTTPS connection (1): acme-staging.api.letsencrypt.orgFailed authorization procedure. ubock.com (http-01): urn:acme:error:unauthorized :: The client lacks sufficient authorization :: Invalid response from http://ubock.com/.well-known/acme-challenge/N0RmkJZzCapvbUkwlsyGE_7D-tj-bl6FidIQy4zPUFI [139.0.0.0]: 404
IMPORTANT NOTES:
- If you lose your account credentials, you can recover through
e-mails sent to u@ubock.com.
- The following errors were reported by the server:
Domain: ubock.com
Type: unauthorized
Detail: Invalid response from
http://ubock.com/.well-known/acme-challenge/N0RmkJZzCapvbUkwlsyGE_7D-tj-bl6FidIQy4zPUFI
[139.0.0.0]: 404
To fix these errors, please make sure that your domain name was
entered correctly and the DNS A record(s) for that domain
contain(s) the right IP address.
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.location ~ /.well-known {
allow all;
}IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/ubock.com/fullchain.pem. Your cert will
expire on 2017-05-27. To obtain a new or tweaked version of this
certificate in the future, simply run certbot again. To
non-interactively renew all of your certificates, run "certbot
renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let‘s Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
chain.pem - Apache根证书和中继证书
fullchain.pem - Nginx所需要ssl_certificate文件
privkey.pem - 安全证书KEY文件部署证书到Nginx
upstream tomcats{
server 127.0.0.1:8080;
}
# Settings for a TLS enabled server.
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name www.ubock.com ubock.com;
root /usr/share/nginx/html;
index index.html index.htm;
ssl_certificate "/etc/letsencrypt/live/ubock.com/fullchain.pem";#证书文件
ssl_certificate_key "/etc/letsencrypt/live/ubock.com/privkey.pem";#证书KEY文件
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; #按照这个协议配置
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:HIGH:!aNULL:!MD5:!RC4:!DHE; #按照这个套件配置
ssl_prefer_server_ciphers on;
# Load configuration files for the default server block.
include /etc/nginx/default.d/.conf;
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_set_header X-Forwarded-Proto https;
proxy_redirect off;
proxy_pass http://tomcats;#负载服务器
}
error_page 404 /404.html;
location = /40x.html {
}
error_page 500 502 503 504 /50x.html;
location = /50x.html {
}
}
重新启动nginx服务:systemctl restart nginx
打开网页就会看地址栏前个安全锁图标: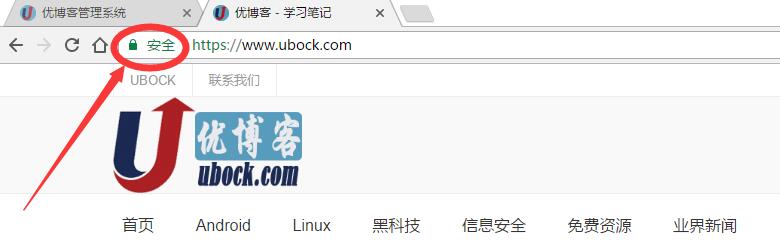
location / {
rewrite ^(.*) https://$host$1 permanent;
}
location ~ /.well-known {
allow all;
}证书自动续期
certbot renew --dry-run [root@VM_151_73_centos ~]# certbot renew --dry-run
Saving debug log to /var/log/letsencrypt/letsencrypt.log
-------------------------------------------------------------------------------
Processing /etc/letsencrypt/renewal/ubock.com.conf
-------------------------------------------------------------------------------
Cert not due for renewal, but simulating renewal for dry run
Starting new HTTPS connection (1): acme-staging.api.letsencrypt.org
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for ubock.com
http-01 challenge for www.ubock.com
Waiting for verification...
Cleaning up challenges
Generating key (2048 bits): /etc/letsencrypt/keys/0001_key-certbot.pem
Creating CSR: /etc/letsencrypt/csr/0001_csr-certbot.pem
DRY RUN: simulating ‘certbot renew‘ close to cert expiry (The test certificates below have not been saved.)
Congratulations, all renewals succeeded. The following certs have been renewed:
/etc/letsencrypt/live/ubock.com/fullchain.pem (success)
DRY RUN: simulating ‘certbot renew‘ close to cert expiry (The test certificates above have not been saved.)
IMPORTANT NOTES:
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
在系统中添加周期性执行更新证书任务命令
crontab -e
在最后添加如下命令:30 4 * * 1 certbot renew --renew-hook "systemctl restart nginx" --quiet > /dev/null 2>&1 &
修改好后保存退出。
文章标题:SSL证书 - Let's Encrypt 证书部署 HTTPS
文章链接:http://soscw.com/index.php/essay/39512.html