基于C# 的RSA 前端JS加密后端进行解密。
2021-02-15 15:24
标签:system back data expect add new substr ... you 前端代码 引用 js : 将加密后的信息,和加密KEY的主键传回登录接口 获取解密Key,对加密信息进行解密 引用 using System.Security.Cryptography; 解密 生成密钥对 基于C# 的RSA 前端JS加密后端进行解密。 标签:system back data expect add new substr ... you 原文地址:https://www.cnblogs.com/yyyuguo/p/8426716.htmlhttp://passport.cnblogs.com/scripts/jsencrypt.min.js
通过接口从服务端获取随机一对密钥串,主键为Token function GetRSAKey(params, callback) {
Service.post({
url: "/BaseService.svc/GetRSAKey",
params: {
},
success: function (response) {
var encrypt = new JSEncrypt();
encrypt.setPublicKey(response.PublicKey);
params = JSON.stringify(params);
var Encryptdata = encrypt.encrypt(params);
//+号的处理:因为数据在网络上传输时,非字母数字字符都将被替换成百分号(%)后跟两位十六进制数,
//而base64编码在传输到后端的时候,+会变成空格,因此先替换掉。后端再替换回来
Encryptdata = encodeURI(Encryptdata).replace(/\+/g, ‘%2B‘);
if (callback) {
callback(Encryptdata, response.Token);
}
}
});
}
GetRSAKey(params, function (Encryptdata, token) {
Service.post({
url: "/UserAccountService.svc/SafeInDoor",
params: {
Encryptdata: Encryptdata,
Token: token,
},
success: function (response) {
if (response.Token) {
} else {
ZENG.msgbox.show(response.StatusText, 5, 2000);
}
},
error: function (response) {
},
mask: function () {
$("#J_LoginSub").mask("正在登录,请稍候...");
},
unmask: function () {
$("#J_LoginSub").unmask();
}
});
})
}
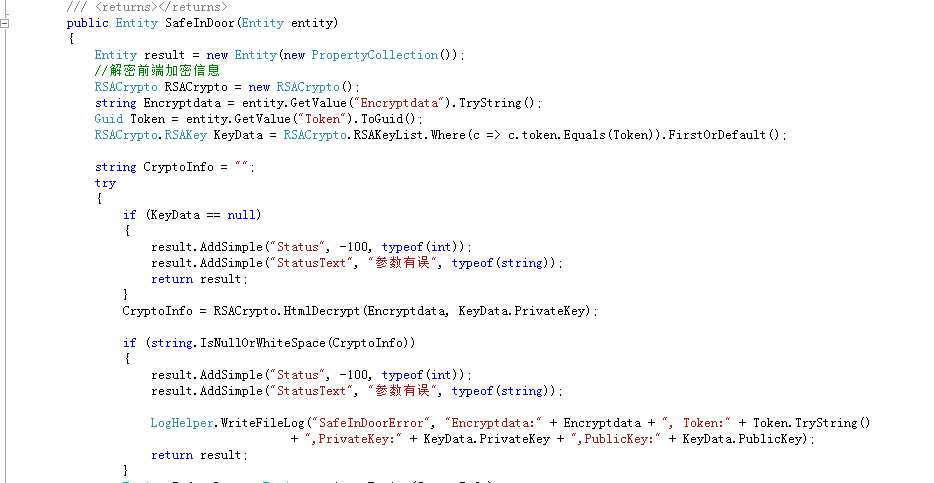
using Cn.Ubingo.Security.RSA.Key; ///
private RSACryptoServiceProvider CreateRsaProviderFromPrivateKey(string privateKey)
{
var privateKeyBits = System.Convert.FromBase64String(privateKey);
var RSA = new RSACryptoServiceProvider();
var RSAparams = new RSAParameters();
using (BinaryReader binr = new BinaryReader(new MemoryStream(privateKeyBits)))
{
byte bt = 0;
ushort twobytes = 0;
twobytes = binr.ReadUInt16();
if (twobytes == 0x8130)
binr.ReadByte();
else if (twobytes == 0x8230)
binr.ReadInt16();
else
throw new Exception("Unexpected value read binr.ReadUInt16()");
twobytes = binr.ReadUInt16();
if (twobytes != 0x0102)
throw new Exception("Unexpected version");
bt = binr.ReadByte();
if (bt != 0x00)
throw new Exception("Unexpected value read binr.ReadByte()");
RSAparams.Modulus = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Exponent = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.D = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.P = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.Q = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DP = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.DQ = binr.ReadBytes(GetIntegerSize(binr));
RSAparams.InverseQ = binr.ReadBytes(GetIntegerSize(binr));
}
RSA.ImportParameters(RSAparams);
return RSA;
}
private int GetIntegerSize(BinaryReader binr)
{
byte bt = 0;
byte lowbyte = 0x00;
byte highbyte = 0x00;
int count = 0;
bt = binr.ReadByte();
if (bt != 0x02)
return 0;
bt = binr.ReadByte();
if (bt == 0x81)
count = binr.ReadByte();
else
if (bt == 0x82)
{
highbyte = binr.ReadByte();
lowbyte = binr.ReadByte();
byte[] modint = { lowbyte, highbyte, 0x00, 0x00 };
count = BitConverter.ToInt32(modint, 0);
}
else
{
count = bt;
}
while (binr.ReadByte() == 0x00)
{
count -= 1;
}
binr.BaseStream.Seek(-1, SeekOrigin.Current);
return count;
}
///
下一篇:C# Redis应用
文章标题:基于C# 的RSA 前端JS加密后端进行解密。
文章链接:http://soscw.com/index.php/essay/55715.html