traefik Ingress https配置
2021-02-17 19:17
标签:rbac 策略 extension test tom windows alt set name 在 RBAC API 的四个重要概念: traefik目前主要有2个版本,分别是1.x和2.x。因为2个版本之间,配置文件差异比较大,目前网络上的博客文章都是基于1.x编写的。 因此,本文采用1.x最后一个版本,镜像名为:traefik:v1.7.24-alpine https证书,是从阿里云购买的,买的通配符证书,1年1千多块钱左右。 登录master节点,创建证书目录。 将证书上传到此目录,并重命名文件。 目录结构如下: 创建secret,保存https证书,注意操作目录,如果不是在此目录下操作,须指定绝对路径。 如果需要配置traefik多域名证书形式,traefik能够自动识别证书。请参考文章底部提供的参考链接! 为 k8s-node01 节点指定label标签为edgenode=true 这里面包含了rbac,DaemonSet,controller,traefik UI,https配置,configmap 使用DaemonSet类型来部署Traefik,并使用nodeSelector来限定Traefik所部署的主机。如果有dns,将域名解析到这所部署的主机即可。 开始部署 由于内网没有dns服务器,直接修改windows10的hosts文件,添加一条记录。 注意:这里的10.212.20.240是Traefik所部署的主机。不是master节点ip 访问http和https 效果如下: 现在k8s环境中,有一个vue开发的web后台。 查看pod 查看svc 目前的service类型是ClusterIP 新建一个yaml,通过traefik来暴露访问。 wxbweb-traefik.yaml 发布一下 新增一条hosts记录 访问页面是否正常。 2.0配置,请参考 https://docs.traefik.io/user-guides/crd-acme/ 本文参考链接: https://www.cnblogs.com/cptao/p/10911918.html traefik Ingress https配置 标签:rbac 策略 extension test tom windows alt set name 原文地址:https://www.cnblogs.com/xiao987334176/p/12937537.html一、概述
1、理解Ingress
2、理解Ingress Controller
3、RBAC
二、部署traefik
环境介绍
系统
k8s版本
docker
ip
主机名
配置
centos 7.6
1.18.1
19.03.5
10.212.20.94
k8s-master
2核4G
centos 7.6
1.18.1
19.03.5
10.212.20.240
k8s-node01
2核8G
traefik版本
配置证书
mkdir /etc/kubernetes/ssl
./
├── tls.crt
└── tls.key
创建secret
cd /etc/kubernetes/ssl
kubectl create secret generic ssl --from-file=tls.crt --from-file=tls.key -n kube-system
打label标签
kubectl label nodes k8s-node01 edgenode=true
配置yaml
traefik.yaml


---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
rules:
- apiGroups:
- ""
resources:
- services
- endpoints
- secrets
verbs:
- get
- list
- watch
- apiGroups:
- extensions
resources:
- ingresses
verbs:
- get
- list
- watch
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: traefik-ingress-controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: traefik-ingress-controller
subjects:
- kind: ServiceAccount
name: traefik-ingress-controller
namespace: kube-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: traefik-ingress-controller
namespace: kube-system
---
kind: ConfigMap
apiVersion: v1
metadata:
name: traefik-conf
namespace: kube-system
data:
traefik.toml: |
insecureSkipVerify = true
defaultEntryPoints = ["http","https"]
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.https]
address = ":443"
[entryPoints.https.tls]
[[entryPoints.https.tls.certificates]]
CertFile = "/ssl/tls.crt"
KeyFile = "/ssl/tls.key"
---
kind: DaemonSet
apiVersion: apps/v1
metadata:
name: traefik-ingress-controller
namespace: kube-system
labels:
k8s-app: traefik-ingress-lb
spec:
selector:
matchLabels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
template:
metadata:
labels:
k8s-app: traefik-ingress-lb
name: traefik-ingress-lb
spec:
serviceAccountName: traefik-ingress-controller
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
terminationGracePeriodSeconds: 60
hostNetwork: true
#nodeSelector:
# ingress: traefik
volumes:
- name: ssl
secret:
secretName: ssl
- name: config
configMap:
name: traefik-conf
containers:
- image: traefik:v1.7.24-alpine
name: traefik-ingress-lb
ports:
- name: http
containerPort: 80
hostPort: 80
- name: admin
containerPort: 8080
securityContext:
privileged: true
args:
- --configfile=/config/traefik.toml
- -d
- --web
- --kubernetes
volumeMounts:
- mountPath: "/ssl"
name: "ssl"
- mountPath: "/config"
name: "config"
nodeSelector:
edgenode: "true"
---
kind: Service
apiVersion: v1
metadata:
name: traefik-ingress-service
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- protocol: TCP
port: 80
name: web
- protocol: TCP
port: 8080
name: admin
- protocol: TCP
port: 443
name: https
type: NodePort
---
apiVersion: v1
kind: Service
metadata:
name: traefik-web-ui
namespace: kube-system
spec:
selector:
k8s-app: traefik-ingress-lb
ports:
- port: 80
targetPort: 8080
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: traefik-web-ui
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: traefikui.test.com
http:
paths:
- backend:
serviceName: traefik-web-ui
servicePort: 80
kubectl apply -f traefik.yaml
访问traefik ui
10.212.20.240 traefikui.test.com
http://traefikui.test.com
https://traefikui.test.com
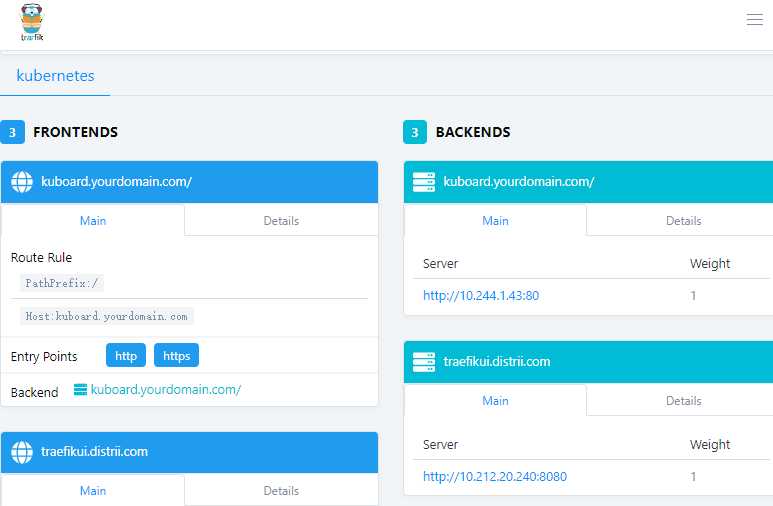
三、traefik发布应用
# kubectl get pods -n test
NAME READY STATUS RESTARTS AGE
web-wxbweb-845994566c-4dcxt 1/1 Running 2 2d23h
# kubectl get svc -n test
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
web-wxbweb ClusterIP 10.1.43.224
kind: Ingress
metadata:
name: web-wxbweb
namespace: test
annotations:
kubernetes.io/ingress.class: traefik
traefik.frontend.rule.type: PathPrefixStrip
spec:
rules:
- host: wxbweb.test.com
http:
paths:
- path: /
backend:
serviceName: web-wxbweb
servicePort: 7000
kubectl apply -f wxbweb-traefik.yaml
10.212.20.240 wxbweb.test.com
文章标题:traefik Ingress https配置
文章链接:http://soscw.com/index.php/essay/56700.html