标签:space database cfa nts c11 bdc nbsp dea cdb
How Does Navicat Encrypt Password?
This repo will tell you how Navicat encrypts password and offer a tool to reveal passwords encrypted by Navicat.
1. What is Navicat?
Navicat is a series of graphical database management and development software produced by PremiumSoft CyberTech Ltd. for MySQL, MariaDB, Oracle, SQLite, PostgreSQL and Microsoft SQL Server.
It has an Explorer-like graphical user interface and supports multiple database connections for local and remote databases. Its design is made to meet the needs of a variety of audiences, from database administrators and programmers to various businesses/companies that serve clients and share information with partners.
2. What does indicate that Navicat encrypts password?
If you use Navicat to manage one of your databases, the first thing you should do is to create a connection to the database. So that means you should fill textboxes on the window showed below with the database‘s information like Host name, User name, Password and so on.
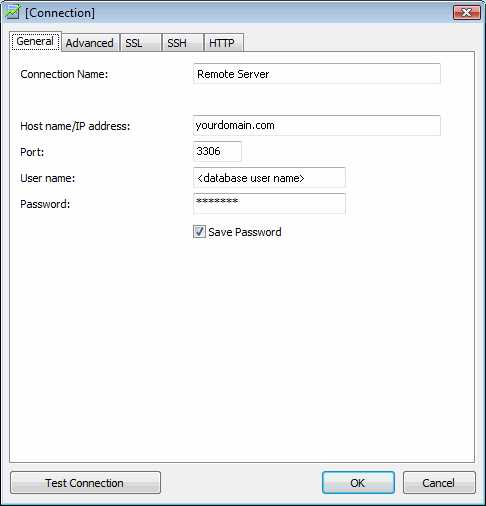
If you check "Save Password", after you click "Ok" button, Navicat will encrypt the password and then save the connection configuration, containing encrypted password, in Windows Registry. The exact path is showed below:
| Database Type |
Path |
| MySQL |
HKEY_CURRENT_USER\Software\PremiumSoft\Navicat\Servers\ |
| MariaDB |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatMARIADB\Servers\ |
| MongoDB |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatMONGODB\Servers\ |
| Microsoft SQL |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatMSSQL\Servers\ |
| Oracle |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatOra\Servers\ |
| PostgreSQL |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatPG\Servers\ |
| SQLite |
HKEY_CURRENT_USER\Software\PremiumSoft\NavicatSQLite\Servers\ |
The following is an example:
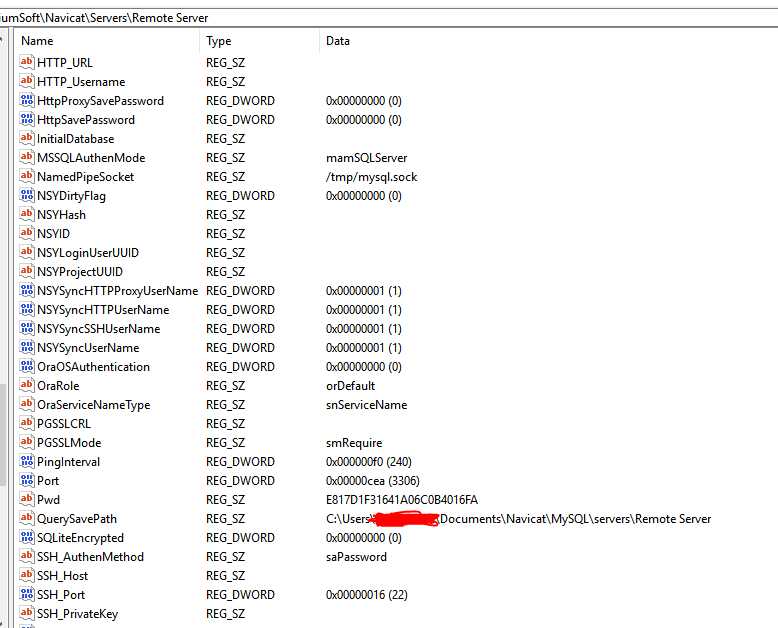
3. How does Navicat encrypt password?
See here.
4. How to use the sample code in python3 folder?
-
Please make sure that you have Python3.
-
Please make sure that you have pycryptodome module if you want to use NavicatCipher.py and NcxReader.py.
You can install pycryptodome module by command:
$ pip install pycryptodome
-
Please make sure that you have pypiwin32 module if you want to use ShowNavicat.py.
You can install pypiwin32 module by command:
-
NavicatCipher.py
Usage:
NavicatCrypto.py [-ncx] <enc> "enc" for encryption, "dec" for decryption.
This parameter must be specified.
[-ncx] Indicate that plaintext/ciphertext is
prepared for/exported from NCX file.
This parameter is optional.
<plaintext> Plaintext string or ciphertext string.
NOTICE: Ciphertext string must be a hex string.
This parameter must be specified.
</plaintext></enc></plaintext></enc></code></pre>
<p>Example:</p>
<div>
<pre>$ <span>./NavicatCipher.py enc <span><span>"This is a test<span>"
<span>0EA71F51DD37BFB60CCBA219BE3A
$ <span>./NavicatCipher.py dec 0EA71F51DD37BFB60CCBA219BE3A
<span>This is a test
$ <span>./NavicatCipher.py enc -ncx <span><span>"This is a test<span>"
<span>B75D320B6211468D63EB3B67C9E85933
$ <span>./NavicatCipher.py dec -ncx B75D320B6211468D63EB3B67C9E85933
<span>This is a test
$ <span>python3
<span>Python 3.6.7 (default, Oct 22 2018, 11:32:17)
<span>[GCC 8.2.0] on linux
<span>Type "help", "copyright", "credits" or "license" for more information.
<span>&gt;&gt;&gt; from NavicatCipher import *
<span>&gt;&gt;&gt; cipher = Navicat12Crypto()
<span>&gt;&gt;&gt; cipher.EncryptString(‘This is a test‘)
<span>‘0EA71F51DD37BFB60CCBA219BE3A‘
<span>&gt;&gt;&gt; cipher.DecryptString(‘0EA71F51DD37BFB60CCBA219BE3A‘)
<span>‘This is a test‘
<span>&gt;&gt;&gt; cipher.EncryptStringForNCX(‘This is a test‘)
<span>‘B75D320B6211468D63EB3B67C9E85933‘
<span>&gt;&gt;&gt; cipher.DecryptStringForNCX(‘B75D320B6211468D63EB3B67C9E85933‘)
<span>‘This is a test‘</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></pre>
</div>
</li>
<li contentscore="69">
<p>NcxReader.py</p>
<p>Show database servers‘ information inside <code>*.ncx</code> file.</p>
<pre><code>Usage:
NcxReader.py <path to ncx file></path></code></pre>
<p>Example:</p>
<div>
<pre>$ <span>./NcxReader <span>~/connectioms.ncx
<span>-----------------xxxxxxxxxxxx--------------------
<span>Connection Type = MYSQL
<span>Host = localhost
<span>Port = 3306
<span>UserName = root
<span>Password = 12345678
<span>------------------yyyyyyyyyy---------------------
<span>Connection Type = MYSQL
<span>Host = example.com
<span>Port = 3306
<span>UserName = server
<span>Password = 0000000000
<span>...
<span>...
<span>...</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></pre>
</div>
</li>
<li contentscore="102">
<p>ShowNavicat.py</p>
<p>Just run it in Windows. It will list all Navicat configurations inside Windows Registry.</p>
<p>Example:</p>
<div contentscore="77">
<pre><span>&gt;ShowNavicat.py
<span>+--------------------------------------------------+
<span>| MySQL Server |
<span>+--------------------------------------------------+
<span>Host: example.com
<span>Port: 3306
<span>Username: server
<span>Password: 0000000000
<span>...
<span>...
<span>+--------------------------------------------------+
<span>| MariaDB Server |
<span>+--------------------------------------------------+
<span>...
<span>...
<span>+--------------------------------------------------+
<span>| MongoDB Server |
<span>+--------------------------------------------------+
<span>...
<span>...
<span>...<br><br><span><strong>Blowfish.cs</strong></span><br></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></pre>
<div>
<pre><span>using</span><span> System;
</span><span>namespace</span><span> NavicatCrypto {
</span><span>class</span><span> Blowfish {
</span><span>public</span> <span>enum</span><span> Endian { Little, Big };
</span><span>public</span> <span>static</span> <span>readonly</span> <span>int</span> MinUserKeyLength = <span>1</span><span>;
</span><span>public</span> <span>static</span> <span>readonly</span> <span>int</span> MaxUserKeyLength = <span>56</span><span>;
</span><span>public</span> <span>static</span> <span>readonly</span> <span>int</span> BlockSize = <span>8</span><span>;
</span><span>private</span> <span>static</span> <span>readonly</span> UInt32[] OriginPBox = <span>new</span><span> UInt32[] {
</span><span>0x243F6A88</span>, <span>0x85A308D3</span>, <span>0x13198A2E</span>, <span>0x03707344</span>, <span>0xA4093822</span>, <span>0x299F31D0</span><span>,
</span><span>0x082EFA98</span>, <span>0xEC4E6C89</span>, <span>0x452821E6</span>, <span>0x38D01377</span>, <span>0xBE5466CF</span>, <span>0x34E90C6C</span><span>,
</span><span>0xC0AC29B7</span>, <span>0xC97C50DD</span>, <span>0x3F84D5B5</span>, <span>0xB5470917</span>, <span>0x9216D5D9</span>, <span>0x8979FB1B</span><span>
};
</span><span>private</span> <span>static</span> <span>readonly</span> UInt32[,] OriginSBox = <span>new</span> UInt32[<span>4</span>, <span>256</span><span>] {
{
</span><span>0xD1310BA6</span>, <span>0x98DFB5AC</span>, <span>0x2FFD72DB</span>, <span>0xD01ADFB7</span>, <span>0xB8E1AFED</span>, <span>0x6A267E96</span>, <span>0xBA7C9045</span>, <span>0xF12C7F99</span>, <span>0x24A19947</span>, <span>0xB3916CF7</span>, <span>0x0801F2E2</span>, <span>0x858EFC16</span>, <span>0x636920D8</span>, <span>0x71574E69</span>, <span>0xA458FEA3</span>, <span>0xF4933D7E</span><span>,
</span><span>0x0D95748F</span>, <span>0x728EB658</span>, <span>0x718BCD58</span>, <span>0x82154AEE</span>, <span>0x7B54A41D</span>, <span>0xC25A59B5</span>, <span>0x9C30D539</span>, <span>0x2AF26013</span>, <span>0xC5D1B023</span>, <span>0x286085F0</span>, <span>0xCA417918</span>, <span>0xB8DB38EF</span>, <span>0x8E79DCB0</span>, <span>0x603A180E</span>, <span>0x6C9E0E8B</span>, <span>0xB01E8A3E</span><span>,
</span><span>0xD71577C1</span>, <span>0xBD314B27</span>, <span>0x78AF2FDA</span>, <span>0x55605C60</span>, <span>0xE65525F3</span>, <span>0xAA55AB94</span>, <span>0x57489862</span>, <span>0x63E81440</span>, <span>0x55CA396A</span>, <span>0x2AAB10B6</span>, <span>0xB4CC5C34</span>, <span>0x1141E8CE</span>, <span>0xA15486AF</span>, <span>0x7C72E993</span>, <span>0xB3EE1411</span>, <span>0x636FBC2A</span><span>,
</span><span>0x2BA9C55D</span>, <span>0x741831F6</span>, <span>0xCE5C3E16</span>, <span>0x9B87931E</span>, <span>0xAFD6BA33</span>, <span>0x6C24CF5C</span>, <span>0x7A325381</span>, <span>0x28958677</span>, <span>0x3B8F4898</span>, <span>0x6B4BB9AF</span>, <span>0xC4BFE81B</span>, <span>0x66282193</span>, <span>0x61D809CC</span>, <span>0xFB21A991</span>, <span>0x487CAC60</span>, <span>0x5DEC8032</span><span>,
</span><span>0xEF845D5D</span>, <span>0xE98575B1</span>, <span>0xDC262302</span>, <span>0xEB651B88</span>, <span>0x23893E81</span>, <span>0xD396ACC5</span>, <span>0x0F6D6FF3</span>, <span>0x83F44239</span>, <span>0x2E0B4482</span>, <span>0xA4842004</span>, <span>0x69C8F04A</span>, <span>0x9E1F9B5E</span>, <span>0x21C66842</span>, <span>0xF6E96C9A</span>, <span>0x670C9C61</span>, <span>0xABD388F0</span><span>,
</span><span>0x6A51A0D2</span>, <span>0xD8542F68</span>, <span>0x960FA728</span>, <span>0xAB5133A3</span>, <span>0x6EEF0B6C</span>, <span>0x137A3BE4</span>, <span>0xBA3BF050</span>, <span>0x7EFB2A98</span>, <span>0xA1F1651D</span>, <span>0x39AF0176</span>, <span>0x66CA593E</span>, <span>0x82430E88</span>, <span>0x8CEE8619</span>, <span>0x456F9FB4</span>, <span>0x7D84A5C3</span>, <span>0x3B8B5EBE</span><span>,
</span><span>0xE06F75D8</span>, <span>0x85C12073</span>, <span>0x401A449F</span>, <span>0x56C16AA6</span>, <span>0x4ED3AA62</span>, <span>0x363F7706</span>, <span>0x1BFEDF72</span>, <span>0x429B023D</span>, <span>0x37D0D724</span>, <span>0xD00A1248</span>, <span>0xDB0FEAD3</span>, <span>0x49F1C09B</span>, <span>0x075372C9</span>, <span>0x80991B7B</span>, <span>0x25D479D8</span>, <span>0xF6E8DEF7</span><span>,
</span><span>0xE3FE501A</span>, <span>0xB6794C3B</span>, <span>0x976CE0BD</span>, <span>0x04C006BA</span>, <span>0xC1A94FB6</span>, <span>0x409F60C4</span>, <span>0x5E5C9EC2</span>, <span>0x196A2463</span>, <span>0x68FB6FAF</span>, <span>0x3E6C53B5</span>, <span>0x1339B2EB</span>, <span>0x3B52EC6F</span>, <span>0x6DFC511F</span>, <span>0x9B30952C</span>, <span>0xCC814544</span>, <span>0xAF5EBD09</span><span>,
</span><span>0xBEE3D004</span>, <span>0xDE334AFD</span>, <span>0x660F2807</span>, <span>0x192E4BB3</span>, <span>0xC0CBA857</span>, <span>0x45C8740F</span>, <span>0xD20B5F39</span>, <span>0xB9D3FBDB</span>, <span>0x5579C0BD</span>, <span>0x1A60320A</span>, <span>0xD6A100C6</span>, <span>0x402C7279</span>, <span>0x679F25FE</span>, <span>0xFB1FA3CC</span>, <span>0x8EA5E9F8</span>, <span>0xDB3222F8</span><span>,
</span><span>0x3C7516DF</span>, <span>0xFD616B15</span>, <span>0x2F501EC8</span>, <span>0xAD0552AB</span>, <span>0x323DB5FA</span>, <span>0xFD238760</span>, <span>0x53317B48</span>, <span>0x3E00DF82</span>, <span>0x9E5C57BB</span>, <span>0xCA6F8CA0</span>, <span>0x1A87562E</span>, <span>0xDF1769DB</span>, <span>0xD542A8F6</span>, <span>0x287EFFC3</span>, <span>0xAC6732C6</span>, <span>0x8C4F5573</span><span>,
</span><span>0x695B27B0</span>, <span>0xBBCA58C8</span>, <span>0xE1FFA35D</span>, <span>0xB8F011A0</span>, <span>0x10FA3D98</span>, <span>0xFD2183B8</span>, <span>0x4AFCB56C</span>, <span>0x2DD1D35B</span>, <span>0x9A53E479</span>, <span>0xB6F84565</span>, <span>0xD28E49BC</span>, <span>0x4BFB9790</span>, <span>0xE1DDF2DA</span>, <span>0xA4CB7E33</span>, <span>0x62FB1341</span>, <span>0xCEE4C6E8</span><span>,
</span><span>0xEF20CADA</span>, <span>0x36774C01</span>, <span>0xD07E9EFE</span>, <span>0x2BF11FB4</span>, <span>0x95DBDA4D</span>, <span>0xAE909198</span>, <span>0xEAAD8E71</span>, <span>0x6B93D5A0</span>, <span>0xD08ED1D0</span>, <span>0xAFC725E0</span>, <span>0x8E3C5B2F</span>, <span>0x8E7594B7</span>, <span>0x8FF6E2FB</span>, <span>0xF2122B64</span>, <span>0x8888B812</span>, <span>0x900DF01C</span><span>,
</span><span>0x4FAD5EA0</span>, <span>0x688FC31C</span>, <span>0xD1CFF191</span>, <span>0xB3A8C1AD</span>, <span>0x2F2F2218</span>, <span>0xBE0E1777</span>, <span>0xEA752DFE</span>, <span>0x8B021FA1</span>, <span>0xE5A0CC0F</span>, <span>0xB56F74E8</span>, <span>0x18ACF3D6</span>, <span>0xCE89E299</span>, <span>0xB4A84FE0</span>, <span>0xFD13E0B7</span>, <span>0x7CC43B81</span>, <span>0xD2ADA8D9</span><span>,
</span><span>0x165FA266</span>, <span>0x80957705</span>, <span>0x93CC7314</span>, <span>0x211A1477</span>, <span>0xE6AD2065</span>, <span>0x77B5FA86</span>, <span>0xC75442F5</span>, <span>0xFB9D35CF</span>, <span>0xEBCDAF0C</span>, <span>0x7B3E89A0</span>, <span>0xD6411BD3</span>, <span>0xAE1E7E49</span>, <span>0x00250E2D</span>, <span>0x2071B35E</span>, <span>0x226800BB</span>, <span>0x57B8E0AF</span><span>,
</span><span>0x2464369B</span>, <span>0xF009B91E</span>, <span>0x5563911D</span>, <span>0x59DFA6AA</span>, <span>0x78C14389</span>, <span>0xD95A537F</span>, <span>0x207D5BA2</span>, <span>0x02E5B9C5</span>, <span>0x83260376</span>, <span>0x6295CFA9</span>, <span>0x11C81968</span>, <span>0x4E734A41</span>, <span>0xB3472DCA</span>, <span>0x7B14A94A</span>, <span>0x1B510052</span>, <span>0x9A532915</span><span>,
</span><span>0xD60F573F</span>, <span>0xBC9BC6E4</span>, <span>0x2B60A476</span>, <span>0x81E67400</span>, <span>0x08BA6FB5</span>, <span>0x571BE91F</span>, <span>0xF296EC6B</span>, <span>0x2A0DD915</span>, <span>0xB6636521</span>, <span>0xE7B9F9B6</span>, <span>0xFF34052E</span>, <span>0xC5855664</span>, <span>0x53B02D5D</span>, <span>0xA99F8FA1</span>, <span>0x08BA4799</span>, <span>0x6E85076A</span><span>
},
{
</span><span>0x4B7A70E9</span>, <span>0xB5B32944</span>, <span>0xDB75092E</span>, <span>0xC4192623</span>, <span>0xAD6EA6B0</span>, <span>0x49A7DF7D</span>, <span>0x9CEE60B8</span>, <span>0x8FEDB266</span>, <span>0xECAA8C71</span>, <span>0x699A17FF</span>, <span>0x5664526C</span>, <span>0xC2B19EE1</span>, <span>0x193602A5</span>, <span>0x75094C29</span>, <span>0xA0591340</span>, <span>0xE4183A3E</span><span>,
</span><span>0x3F54989A</span>, <span>0x5B429D65</span>, <span>0x6B8FE4D6</span>, <span>0x99F73FD6</span>, <span>0xA1D29C07</span>, <span>0xEFE830F5</span>, <span>0x4D2D38E6</span>, <span>0xF0255DC1</span>, <span>0x4CDD2086</span>, <span>0x8470EB26</span>, <span>0x6382E9C6</span>, <span>0x021ECC5E</span>, <span>0x09686B3F</span>, <span>0x3EBAEFC9</span>, <span>0x3C971814</span>, <span>0x6B6A70A1</span><span>,
</span><span>0x687F3584</span>, <span>0x52A0E286</span>, <span>0xB79C5305</span>, <span>0xAA500737</span>, <span>0x3E07841C</span>, <span>0x7FDEAE5C</span>, <span>0x8E7D44EC</span>, <span>0x5716F2B8</span>, <span>0xB03ADA37</span>, <span>0xF0500C0D</span>, <span>0xF01C1F04</span>, <span>0x0200B3FF</span>, <span>0xAE0CF51A</span>, <span>0x3CB574B2</span>, <span>0x25837A58</span>, <span>0xDC0921BD</span><span>,
</span><span>0xD19113F9</span>, <span>0x7CA92FF6</span>, <span>0x94324773</span>, <span>0x22F54701</span>, <span>0x3AE5E581</span>, <span>0x37C2DADC</span>, <span>0xC8B57634</span>, <span>0x9AF3DDA7</span>, <span>0xA9446146</span>, <span>0x0FD0030E</span>, <span>0xECC8C73E</span>, <span>0xA4751E41</span>, <span>0xE238CD99</span>, <span>0x3BEA0E2F</span>, <span>0x3280BBA1</span>, <span>0x183EB331</span><span>,
</span><span>0x4E548B38</span>, <span>0x4F6DB908</span>, <span>0x6F420D03</span>, <span>0xF60A04BF</span>, <span>0x2CB81290</span>, <span>0x24977C79</span>, <span>0x5679B072</span>, <span>0xBCAF89AF</span>, <span>0xDE9A771F</span>, <span>0xD9930810</span>, <span>0xB38BAE12</span>, <span>0xDCCF3F2E</span>, <span>0x5512721F</span>, <span>0x2E6B7124</span>, <span>0x501ADDE6</span>, <span>0x9F84CD87</span><span>,
</span><span>0x7A584718</span>, <span>0x7408DA17</span>, <span>0xBC9F9ABC</span>, <span>0xE94B7D8C</span>, <span>0xEC7AEC3A</span>, <span>0xDB851DFA</span>, <span>0x63094366</span>, <span>0xC464C3D2</span>, <span>0xEF1C1847</span>, <span>0x3215D908</span>, <span>0xDD433B37</span>, <span>0x24C2BA16</span>, <span>0x12A14D43</span>, <span>0x2A65C451</span>, <span>0x50940002</span>, <span>0x133AE4DD</span><span>,
</span><span>0x71DFF89E</span>, <span>0x10314E55</span>, <span>0x81AC77D6</span>, <span>0x5F11199B</span>, <span>0x043556F1</span>, <span>0xD7A3C76B</span>, <span>0x3C11183B</span>, <span>0x5924A509</span>, <span>0xF28FE6ED</span>, <span>0x97F1FBFA</span>, <span>0x9EBABF2C</span>, <span>0x1E153C6E</span>, <span>0x86E34570</span>, <span>0xEAE96FB1</span>, <span>0x860E5E0A</span>, <span>0x5A3E2AB3</span><span>,
</span><span>0x771FE71C</span>, <span>0x4E3D06FA</span>, <span>0x2965DCB9</span>, <span>0x99E71D0F</span>, <span>0x803E89D6</span>, <span>0x5266C825</span>, <span>0x2E4CC978</span>, <span>0x9C10B36A</span>, <span>0xC6150EBA</span>, <span>0x94E2EA78</span>, <span>0xA5FC3C53</span>, <span>0x1E0A2DF4</span>, <span>0xF2F74EA7</span>, <span>0x361D2B3D</span>, <span>0x1939260F</span>, <span>0x19C27960</span><span>,
</span><span>0x5223A708</span>, <span>0xF71312B6</span>, <span>0xEBADFE6E</span>, <span>0xEAC31F66</span>, <span>0xE3BC4595</span>, <span>0xA67BC883</span>, <span>0xB17F37D1</span>, <span>0x018CFF28</span>, <span>0xC332DDEF</span>, <span>0xBE6C5AA5</span>, <span>0x65582185</span>, <span>0x68AB9802</span>, <span>0xEECEA50F</span>, <span>0xDB2F953B</span>, <span>0x2AEF7DAD</span>, <span>0x5B6E2F84</span><span>,
</span><span>0x1521B628</span>, <span>0x29076170</span>, <span>0xECDD4775</span>, <span>0x619F1510</span>, <span>0x13CCA830</span>, <span>0xEB61BD96</span>, <span>0x0334FE1E</span>, <span>0xAA0363CF</span>, <span>0xB5735C90</span>, <span>0x4C70A239</span>, <span>0xD59E9E0B</span>, <span>0xCBAADE14</span>, <span>0xEECC86BC</span>, <span>0x60622CA7</span>, <span>0x9CAB5CAB</span>, <span>0xB2F3846E</span><span>,
</span><span>0x648B1EAF</span>, <span>0x19BDF0CA</span>, <span>0xA02369B9</span>, <span>0x655ABB50</span>, <span>0x40685A32</span>, <span>0x3C2AB4B3</span>, <span>0x319EE9D5</span>, <span>0xC021B8F7</span>, <span>0x9B540B19</span>, <span>0x875FA099</span>, <span>0x95F7997E</span>, <span>0x623D7DA8</span>, <span>0xF837889A</span>, <span>0x97E32D77</span>, <span>0x11ED935F</span>, <span>0x16681281</span><span>,
</span><span>0x0E358829</span>, <span>0xC7E61FD6</span>, <span>0x96DEDFA1</span>, <span>0x7858BA99</span>, <span>0x57F584A5</span>, <span>0x1B227263</span>, <span>0x9B83C3FF</span>, <span>0x1AC24696</span>, <span>0xCDB30AEB</span>, <span>0x532E3054</span>, <span>0x8FD948E4</span>, <span>0x6DBC3128</span>, <span>0x58EBF2EF</span>, <span>0x34C6FFEA</span>, <span>0xFE28ED61</span>, <span>0xEE7C3C73</span><span>,
</span><span>0x5D4A14D9</span>, <span>0xE864B7E3</span>, <span>0x42105D14</span>, <span>0x203E13E0</span>, <span>0x45EEE2B6</span>, <span>0xA3AAABEA</span>, <span>0xDB6C4F15</span>, <span>0xFACB4FD0</span>, <span>0xC742F442</span>, <span>0xEF6ABBB5</span>, <span>0x654F3B1D</span>, <span>0x41CD2105</span>, <span>0xD81E799E</span>, <span>0x86854DC7</span>, <span>0xE44B476A</span>, <span>0x3D816250</span><span>,
</span><span>0xCF62A1F2</span>, <span>0x5B8D2646</span>, <span>0xFC8883A0</span>, <span>0xC1C7B6A3</span>, <span>0x7F1524C3</span>, <span>0x69CB7492</span>, <span>0x47848A0B</span>, <span>0x5692B285</span>, <span>0x095BBF00</span>, <span>0xAD19489D</span>, <span>0x1462B174</span>, <span>0x23820E00</span>, <span>0x58428D2A</span>, <span>0x0C55F5EA</span>, <span>0x1DADF43E</span>, <span>0x233F7061</span><span>,
</span><span>0x3372F092</span>, <span>0x8D937E41</span>, <span>0xD65FECF1</span>, <span>0x6C223BDB</span>, <span>0x7CDE3759</span>, <span>0xCBEE7460</span>, <span>0x4085F2A7</span>, <span>0xCE77326E</span>, <span>0xA6078084</span>, <span>0x19F8509E</span>, <span>0xE8EFD855</span>, <span>0x61D99735</span>, <span>0xA969A7AA</span>, <span>0xC50C06C2</span>, <span>0x5A04ABFC</span>, <span>0x800BCADC</span><span>,
</span><span>0x9E447A2E</span>, <span>0xC3453484</span>, <span>0xFDD56705</span>, <span>0x0E1E9EC9</span>, <span>0xDB73DBD3</span>, <span>0x105588CD</span>, <span>0x675FDA79</span>, <span>0xE3674340</span>, <span>0xC5C43465</span>, <span>0x713E38D8</span>, <span>0x3D28F89E</span>, <span>0xF16DFF20</span>, <span>0x153E21E7</span>, <span>0x8FB03D4A</span>, <span>0xE6E39F2B</span>, <span>0xDB83ADF7</span><span>
},
{
</span><span>0xE93D5A68</span>, <span>0x948140F7</span>, <span>0xF64C261C</span>, <span>0x94692934</span>, <span>0x411520F7</span>, <span>0x7602D4F7</span>, <span>0xBCF46B2E</span>, <span>0xD4A20068</span>, <span>0xD4082471</span>, <span>0x3320F46A</span>, <span>0x43B7D4B7</span>, <span>0x500061AF</span>, <span>0x1E39F62E</span>, <span>0x97244546</span>, <span>0x14214F74</span>, <span>0xBF8B8840</span><span>,
</span><span>0x4D95FC1D</span>, <span>0x96B591AF</span>, <span>0x70F4DDD3</span>, <span>0x66A02F45</span>, <span>0xBFBC09EC</span>, <span>0x03BD9785</span>, <span>0x7FAC6DD0</span>, <span>0x31CB8504</span>, <span>0x96EB27B3</span>, <span>0x55FD3941</span>, <span>0xDA2547E6</span>, <span>0xABCA0A9A</span>, <span>0x28507825</span>, <span>0x530429F4</span>, <span>0x0A2C86DA</span>, <span>0xE9B66DFB</span><span>,
</span><span>0x68DC1462</span>, <span>0xD7486900</span>, <span>0x680EC0A4</span>, <span>0x27A18DEE</span>, <span>0x4F3FFEA2</span>, <span>0xE887AD8C</span>, <span>0xB58CE006</span>, <span>0x7AF4D6B6</span>, <span>0xAACE1E7C</span>, <span>0xD3375FEC</span>, <span>0xCE78A399</span>, <span>0x406B2A42</span>, <span>0x20FE9E35</span>, <span>0xD9F385B9</span>, <span>0xEE39D7AB</span>, <span>0x3B124E8B</span><span>,
</span><span>0x1DC9FAF7</span>, <span>0x4B6D1856</span>, <span>0x26A36631</span>, <span>0xEAE397B2</span>, <span>0x3A6EFA74</span>, <span>0xDD5B4332</span>, <span>0x6841E7F7</span>, <span>0xCA7820FB</span>, <span>0xFB0AF54E</span>, <span>0xD8FEB397</span>, <span>0x454056AC</span>, <span>0xBA489527</span>, <span>0x55533A3A</span>, <span>0x20838D87</span>, <span>0xFE6BA9B7</span>, <span>0xD096954B</span><span>,
</span><span>0x55A867BC</span>, <span>0xA1159A58</span>, <span>0xCCA92963</span>, <span>0x99E1DB33</span>, <span>0xA62A4A56</span>, <span>0x3F3125F9</span>, <span>0x5EF47E1C</span>, <span>0x9029317C</span>, <span>0xFDF8E802</span>, <span>0x04272F70</span>, <span>0x80BB155C</span>, <span>0x05282CE3</span>, <span>0x95C11548</span>, <span>0xE4C66D22</span>, <span>0x48C1133F</span>, <span>0xC70F86DC</span><span>,
</span><span>0x07F9C9EE</span>, <span>0x41041F0F</span>, <span>0x404779A4</span>, <span>0x5D886E17</span>, <span>0x325F51EB</span>, <span>0xD59BC0D1</span>, <span>0xF2BCC18F</span>, <span>0x41113564</span>, <span>0x257B7834</span>, <span>0x602A9C60</span>, <span>0xDFF8E8A3</span>, <span>0x1F636C1B</span>, <span>0x0E12B4C2</span>, <span>0x02E1329E</span>, <span>0xAF664FD1</span>, <span>0xCAD18115</span><span>,
</span><span>0x6B2395E0</span>, <span>0x333E92E1</span>, <span>0x3B240B62</span>, <span>0xEEBEB922</span>, <span>0x85B2A20E</span>, <span>0xE6BA0D99</span>, <span>0xDE720C8C</span>, <span>0x2DA2F728</span>, <span>0xD0127845</span>, <span>0x95B794FD</span>, <span>0x647D0862</span>, <span>0xE7CCF5F0</span>, <span>0x5449A36F</span>, <span>0x877D48FA</span>, <span>0xC39DFD27</span>, <span>0xF33E8D1E</span><span>,
</span><span>0x0A476341</span>, <span>0x992EFF74</span>, <span>0x3A6F6EAB</span>, <span>0xF4F8FD37</span>, <span>0xA812DC60</span>, <span>0xA1EBDDF8</span>, <span>0x991BE14C</span>, <span>0xDB6E6B0D</span>, <span>0xC67B5510</span>, <span>0x6D672C37</span>, <span>0x2765D43B</span>, <span>0xDCD0E804</span>, <span>0xF1290DC7</span>, <span>0xCC00FFA3</span>, <span>0xB5390F92</span>, <span>0x690FED0B</span><span>,
</span><span>0x667B9FFB</span>, <span>0xCEDB7D9C</span>, <span>0xA091CF0B</span>, <span>0xD9155EA3</span>, <span>0xBB132F88</span>, <span>0x515BAD24</span>, <span>0x7B9479BF</span>, <span>0x763BD6EB</span>, <span>0x37392EB3</span>, <span>0xCC115979</span>, <span>0x8026E297</span>, <span>0xF42E312D</span>, <span>0x6842ADA7</span>, <span>0xC66A2B3B</span>, <span>0x12754CCC</span>, <span>0x782EF11C</span><span>,
</span><span>0x6A124237</span>, <span>0xB79251E7</span>, <span>0x06A1BBE6</span>, <span>0x4BFB6350</span>, <span>0x1A6B1018</span>, <span>0x11CAEDFA</span>, <span>0x3D25BDD8</span>, <span>0xE2E1C3C9</span>, <span>0x44421659</span>, <span>0x0A121386</span>, <span>0xD90CEC6E</span>, <span>0xD5ABEA2A</span>, <span>0x64AF674E</span>, <span>0xDA86A85F</span>, <span>0xBEBFE988</span>, <span>0x64E4C3FE</span><span>,
</span><span>0x9DBC8057</span>, <span>0xF0F7C086</span>, <span>0x60787BF8</span>, <span>0x6003604D</span>, <span>0xD1FD8346</span>, <span>0xF6381FB0</span>, <span>0x7745AE04</span>, <span>0xD736FCCC</span>, <span>0x83426B33</span>, <span>0xF01EAB71</span>, <span>0xB0804187</span>, <span>0x3C005E5F</span>, <span>0x77A057BE</span>, <span>0xBDE8AE24</span>, <span>0x55464299</span>, <span>0xBF582E61</span><span>,
</span><span>0x4E58F48F</span>, <span>0xF2DDFDA2</span>, <span>0xF474EF38</span>, <span>0x8789BDC2</span>, <span>0x5366F9C3</span>, <span>0xC8B38E74</span>, <span>0xB475F255</span>, <span>0x46FCD9B9</span>, <span>0x7AEB2661</span>, <span>0x8B1DDF84</span>, <span>0x846A0E79</span>, <span>0x915F95E2</span>, <span>0x466E598E</span>, <span>0x20B45770</span>, <span>0x8CD55591</span>, <span>0xC902DE4C</span><span>,
</span><span>0xB90BACE1</span>, <span>0xBB8205D0</span>, <span>0x11A86248</span>, <span>0x7574A99E</span>, <span>0xB77F19B6</span>, <span>0xE0A9DC09</span>, <span>0x662D09A1</span>, <span>0xC4324633</span>, <span>0xE85A1F02</span>, <span>0x09F0BE8C</span>, <span>0x4A99A025</span>, <span>0x1D6EFE10</span>, <span>0x1AB93D1D</span>, <span>0x0BA5A4DF</span>, <span>0xA186F20F</span>, <span>0x2868F169</span><span>,
</span><span>0xDCB7DA83</span>, <span>0x573906FE</span>, <span>0xA1E2CE9B</span>, <span>0x4FCD7F52</span>, <span>0x50115E01</span>, <span>0xA70683FA</span>, <span>0xA002B5C4</span>, <span>0x0DE6D027</span>, <span>0x9AF88C27</span>, <span>0x773F8641</span>, <span>0xC3604C06</span>, <span>0x61A806B5</span>, <span>0xF0177A28</span>, <span>0xC0F586E0</span>, <span>0x006058AA</span>, <span>0x30DC7D62</span><span>,
</span><span>0x11E69ED7</span>, <span>0x2338EA63</span>, <span>0x53C2DD94</span>, <span>0xC2C21634</span>, <span>0xBBCBEE56</span>, <span>0x90BCB6DE</span>, <span>0xEBFC7DA1</span>, <span>0xCE591D76</span>, <span>0x6F05E409</span>, <span>0x4B7C0188</span>, <span>0x39720A3D</span>, <span>0x7C927C24</span>, <span>0x86E3725F</span>, <span>0x724D9DB9</span>, <span>0x1AC15BB4</span>, <span>0xD39EB8FC</span><span>,
</span><span>0xED545578</span>, <span>0x08FCA5B5</span>, <span>0xD83D7CD3</span>, <span>0x4DAD0FC4</span>, <span>0x1E50EF5E</span>, <span>0xB161E6F8</span>, <span>0xA28514D9</span>, <span>0x6C51133C</span>, <span>0x6FD5C7E7</span>, <span>0x56E14EC4</span>, <span>0x362ABFCE</span>, <span>0xDDC6C837</span>, <span>0xD79A3234</span>, <span>0x92638212</span>, <span>0x670EFA8E</span>, <span>0x406000E0</span><span>
},
{
</span><span>0x3A39CE37</span>, <span>0xD3FAF5CF</span>, <span>0xABC27737</span>, <span>0x5AC52D1B</span>, <span>0x5CB0679E</span>, <span>0x4FA33742</span>, <span>0xD3822740</span>, <span>0x99BC9BBE</span>, <span>0xD5118E9D</span>, <span>0xBF0F7315</span>, <span>0xD62D1C7E</span>, <span>0xC700C47B</span>, <span>0xB78C1B6B</span>, <span>0x21A19045</span>, <span>0xB26EB1BE</span>, <span>0x6A366EB4</span><span>,
</span><span>0x5748AB2F</span>, <span>0xBC946E79</span>, <span>0xC6A376D2</span>, <span>0x6549C2C8</span>, <span>0x530FF8EE</span>, <span>0x468DDE7D</span>, <span>0xD5730A1D</span>, <span>0x4CD04DC6</span>, <span>0x2939BBDB</span>, <span>0xA9BA4650</span>, <span>0xAC9526E8</span>, <span>0xBE5EE304</span>, <span>0xA1FAD5F0</span>, <span>0x6A2D519A</span>, <span>0x63EF8CE2</span>, <span>0x9A86EE22</span><span>,
</span><span>0xC089C2B8</span>, <span>0x43242EF6</span>, <span>0xA51E03AA</span>, <span>0x9CF2D0A4</span>, <span>0x83C061BA</span>, <span>0x9BE96A4D</span>, <span>0x8FE51550</span>, <span>0xBA645BD6</span>, <span>0x2826A2F9</span>, <span>0xA73A3AE1</span>, <span>0x4BA99586</span>, <span>0xEF5562E9</span>, <span>0xC72FEFD3</span>, <span>0xF752F7DA</span>, <span>0x3F046F69</span>, <span>0x77FA0A59</span><span>,
</span><span>0x80E4A915</span>, <span>0x87B08601</span>, <span>0x9B09E6AD</span>, <span>0x3B3EE593</span>, <span>0xE990FD5A</span>, <span>0x9E34D797</span>, <span>0x2CF0B7D9</span>, <span>0x022B8B51</span>, <span>0x96D5AC3A</span>, <span>0x017DA67D</span>, <span>0xD1CF3ED6</span>, <span>0x7C7D2D28</span>, <span>0x1F9F25CF</span>, <span>0xADF2B89B</span>, <span>0x5AD6B472</span>, <span>0x5A88F54C</span><span>,
</span><span>0xE029AC71</span>, <span>0xE019A5E6</span>, <span>0x47B0ACFD</span>, <span>0xED93FA9B</span>, <span>0xE8D3C48D</span>, <span>0x283B57CC</span>, <span>0xF8D56629</span>, <span>0x79132E28</span>, <span>0x785F0191</span>, <span>0xED756055</span>, <span>0xF7960E44</span>, <span>0xE3D35E8C</span>, <span>0x15056DD4</span>, <span>0x88F46DBA</span>, <span>0x03A16125</span>, <span>0x0564F0BD</span><span>,
</span><span>0xC3EB9E15</span>, <span>0x3C9057A2</span>, <span>0x97271AEC</span>, <span>0xA93A072A</span>, <span>0x1B3F6D9B</span>, <span>0x1E6321F5</span>, <span>0xF59C66FB</span>, <span>0x26DCF319</span>, <span>0x7533D928</span>, <span>0xB155FDF5</span>, <span>0x03563482</span>, <span>0x8ABA3CBB</span>, <span>0x28517711</span>, <span>0xC20AD9F8</span>, <span>0xABCC5167</span>, <span>0xCCAD925F</span><span>,
</span><span>0x4DE81751</span>, <span>0x3830DC8E</span>, <span>0x379D5862</span>, <span>0x9320F991</span>, <span>0xEA7A90C2</span>, <span>0xFB3E7BCE</span>, <span>0x5121CE64</span>, <span>0x774FBE32</span>, <span>0xA8B6E37E</span>, <span>0xC3293D46</span>, <span>0x48DE5369</span>, <span>0x6413E680</span>, <span>0xA2AE0810</span>, <span>0xDD6DB224</span>, <span>0x69852DFD</span>, <span>0x09072166</span><span>,
</span><span>0xB39A460A</span>, <span>0x6445C0DD</span>, <span>0x586CDECF</span>, <span>0x1C20C8AE</span>, <span>0x5BBEF7DD</span>, <span>0x1B588D40</span>, <span>0xCCD2017F</span>, <span>0x6BB4E3BB</span>, <span>0xDDA26A7E</span>, <span>0x3A59FF45</span>, <span>0x3E350A44</span>, <span>0xBCB4CDD5</span>, <span>0x72EACEA8</span>, <span>0xFA6484BB</span>, <span>0x8D6612AE</span>, <span>0xBF3C6F47</span><span>,
</span><span>0xD29BE463</span>, <span>0x542F5D9E</span>, <span>0xAEC2771B</span>, <span>0xF64E6370</span>, <span>0x740E0D8D</span>, <span>0xE75B1357</span>, <span>0xF8721671</span>, <span>0xAF537D5D</span>, <span>0x4040CB08</span>, <span>0x4EB4E2CC</span>, <span>0x34D2466A</span>, <span>0x0115AF84</span>, <span>0xE1B00428</span>, <span>0x95983A1D</span>, <span>0x06B89FB4</span>, <span>0xCE6EA048</span><span>,
</span><span>0x6F3F3B82</span>, <span>0x3520AB82</span>, <span>0x011A1D4B</span>, <span>0x277227F8</span>, <span>0x611560B1</span>, <span>0xE7933FDC</span>, <span>0xBB3A792B</span>, <span>0x344525BD</span>, <span>0xA08839E1</span>, <span>0x51CE794B</span>, <span>0x2F32C9B7</span>, <span>0xA01FBAC9</span>, <span>0xE01CC87E</span>, <span>0xBCC7D1F6</span>, <span>0xCF0111C3</span>, <span>0xA1E8AAC7</span><span>,
</span><span>0x1A908749</span>, <span>0xD44FBD9A</span>, <span>0xD0DADECB</span>, <span>0xD50ADA38</span>, <span>0x0339C32A</span>, <span>0xC6913667</span>, <span>0x8DF9317C</span>, <span>0xE0B12B4F</span>, <span>0xF79E59B7</span>, <span>0x43F5BB3A</span>, <span>0xF2D519FF</span>, <span>0x27D9459C</span>, <span>0xBF97222C</span>, <span>0x15E6FC2A</span>, <span>0x0F91FC71</span>, <span>0x9B941525</span><span>,
</span><span>0xFAE59361</span>, <span>0xCEB69CEB</span>, <span>0xC2A86459</span>, <span>0x12BAA8D1</span>, <span>0xB6C1075E</span>, <span>0xE3056A0C</span>, <span>0x10D25065</span>, <span>0xCB03A442</span>, <span>0xE0EC6E0E</span>, <span>0x1698DB3B</span>, <span>0x4C98A0BE</span>, <span>0x3278E964</span>, <span>0x9F1F9532</span>, <span>0xE0D392DF</span>, <span>0xD3A0342B</span>, <span>0x8971F21E</span><span>,
</span><span>0x1B0A7441</span>, <span>0x4BA3348C</span>, <span>0xC5BE7120</span>, <span>0xC37632D8</span>, <span>0xDF359F8D</span>, <span>0x9B992F2E</span>, <span>0xE60B6F47</span>, <span>0x0FE3F11D</span>, <span>0xE54CDA54</span>, <span>0x1EDAD891</span>, <span>0xCE6279CF</span>, <span>0xCD3E7E6F</span>, <span>0x1618B166</span>, <span>0xFD2C1D05</span>, <span>0x848FD2C5</span>, <span>0xF6FB2299</span><span>,
</span><span>0xF523F357</span>, <span>0xA6327623</span>, <span>0x93A83531</span>, <span>0x56CCCD02</span>, <span>0xACF08162</span>, <span>0x5A75EBB5</span>, <span>0x6E163697</span>, <span>0x88D273CC</span>, <span>0xDE966292</span>, <span>0x81B949D0</span>, <span>0x4C50901B</span>, <span>0x71C65614</span>, <span>0xE6C6C7BD</span>, <span>0x327A140A</span>, <span>0x45E1D006</span>, <span>0xC3F27B9A</span><span>,
</span><span>0xC9AA53FD</span>, <span>0x62A80F00</span>, <span>0xBB25BFE2</span>, <span>0x35BDD2F6</span>, <span>0x71126905</span>, <span>0xB2040222</span>, <span>0xB6CBCF7C</span>, <span>0xCD769C2B</span>, <span>0x53113EC0</span>, <span>0x1640E3D3</span>, <span>0x38ABBD60</span>, <span>0x2547ADF0</span>, <span>0xBA38209C</span>, <span>0xF746CE76</span>, <span>0x77AFA1C5</span>, <span>0x20756060</span><span>,
</span><span>0x85CBFE4E</span>, <span>0x8AE88DD8</span>, <span>0x7AAAF9B0</span>, <span>0x4CF9AA7E</span>, <span>0x1948C25C</span>, <span>0x02FB8A8C</span>, <span>0x01C36AE4</span>, <span>0xD6EBE1F9</span>, <span>0x90D4F869</span>, <span>0xA65CDEA0</span>, <span>0x3F09252D</span>, <span>0xC208E69F</span>, <span>0xB74E6132</span>, <span>0xCE77E25B</span>, <span>0x578FDFE3</span>, <span>0x3AC372E6</span><span>
}
};
</span><span>private</span><span> UInt32[] SubKey;
</span><span>private</span><span> UInt32[,] SBox;
</span><span>private</span><span> UInt32 _F_Transform(UInt32 x) {
</span><span>byte</span>[] x_bytes =<span> BitConverter.GetBytes(x);
</span><span>if</span> (BitConverter.IsLittleEndian == <span>false</span><span>)
Array.Reverse(x_bytes);
</span><span>return</span> ((SBox[<span>0</span>, x_bytes[<span>3</span>]] + SBox[<span>1</span>, x_bytes[<span>2</span>]]) ^ SBox[<span>2</span>, x_bytes[<span>1</span>]]) +SBox[<span>3</span>, x_bytes[<span>0</span><span>]];
}
</span><span>public</span> <span>void</span> Encrypt(<span>byte</span><span>[] srcBytes, Endian endian) {
</span><span>byte</span>[] L_bytes = <span>new</span> <span>byte</span>[<span>4</span><span>];
</span><span>byte</span>[] R_bytes = <span>new</span> <span>byte</span>[<span>4</span><span>];
Array.Copy(srcBytes, </span><span>0</span>, L_bytes, <span>0</span>, <span>4</span><span>);
Array.Copy(srcBytes, </span><span>4</span>, R_bytes, <span>0</span>, <span>4</span><span>);
</span><span>if</span> (BitConverter.IsLittleEndian &amp;&amp; endian == Endian.Big || BitConverter.IsLittleEndian == <span>false</span> &amp;&amp; endian ==<span> Endian.Little) {
Array.Reverse(L_bytes);
Array.Reverse(R_bytes);
}
UInt32 L </span>= BitConverter.ToUInt32(L_bytes, <span>0</span><span>);
UInt32 R </span>= BitConverter.ToUInt32(R_bytes, <span>0</span><span>);
L </span>^= SubKey[<span>0</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>1</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>2</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>3</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>4</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>5</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>6</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>7</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>8</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>9</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>10</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>11</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>12</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>13</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>14</span><span>];
R </span>^=<span> _F_Transform(L);
R </span>^= SubKey[<span>15</span><span>];
L </span>^=<span> _F_Transform(R);
L </span>^= SubKey[<span>16</span><span>];
R </span>^= SubKey[<span>17</span><span>];
L_bytes </span>=<span> BitConverter.GetBytes(R);
R_bytes </span>=<span> BitConverter.GetBytes(L);
</span><span>if</span> (BitConverter.IsLittleEndian &amp;&amp; endian == Endian.Big || BitConverter.IsLittleEndian == <span>false</span> &amp;&amp; endian ==<span> Endian.Little) {
Array.Reverse(L_bytes);
Array.Reverse(R_bytes);
}
Array.Copy(L_bytes, </span><span>0</span>, srcBytes, <span>0</span>, <span>4</span><span>);
Array.Copy(R_bytes, </span><span>0</span>, srcBytes, <span>4</span>, <span>4</span><span>);
}
</span><span>public</span> <span>void</span> Decrypt(<span>byte</span><span>[] srcBytes, Endian endian) {
</span><span>byte</span>[] L_bytes = <span>new</span> <span>byte</span>[<span>4</span><span>];
</span><span>byte</span>[] R_bytes = <span>new</span> <span>byte</span>[<span>4</span><span>];
Array.Copy(srcBytes, </span><span>0</span>, L_bytes, <span>0</span>, <span>4</span><span>);
Array.Copy(srcBytes, </span><span>4</span>, R_bytes, <span>0</span>, <span>4</span><span>);
</span><span>if</span> (BitConverter.IsLittleEndian &amp;&amp; endian == Endian.Big || BitConverter.IsLittleEndian == <span>false</span> &amp;&amp; endian ==<span> Endian.Little) {
Array.Reverse(L_bytes);
Array.Reverse(R_bytes);
}
UInt32 L </span>= BitConverter.ToUInt32(R_bytes, <span>0</span><span>);
UInt32 R </span>= BitConverter.ToUInt32(L_bytes, <span>0</span><span>);
L </span>^= SubKey[<span>16</span><span>];
R </span>^= SubKey[<span>17</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>15</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>14</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>13</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>12</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>11</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>10</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>9</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>8</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>7</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>6</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>5</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>4</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>3</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>2</span><span>];
L </span>^=<span> _F_Transform(R);
R </span>^= SubKey[<span>1</span><span>];
R </span>^=<span> _F_Transform(L);
L </span>^= SubKey[<span>0</span><span>];
L_bytes </span>=<span> BitConverter.GetBytes(L);
R_bytes </span>=<span> BitConverter.GetBytes(R);
</span><span>if</span> (BitConverter.IsLittleEndian &amp;&amp; endian == Endian.Big || BitConverter.IsLittleEndian == <span>false</span> &amp;&amp; endian ==<span> Endian.Little) {
Array.Reverse(L_bytes);
Array.Reverse(R_bytes);
}
Array.Copy(L_bytes, </span><span>0</span>, srcBytes, <span>0</span>, <span>4</span><span>);
Array.Copy(R_bytes, </span><span>0</span>, srcBytes, <span>4</span>, <span>4</span><span>);
}
</span><span>public</span> Blowfish(<span>byte</span><span>[] UserKey) {
</span><span>if</span> (UserKey.Length MinUserKeyLength)
<span>throw</span> <span>new</span> ArgumentException(<span>"</span><span>UserKey is too short.</span><span>"</span><span>);
</span><span>else</span> <span>if</span> (UserKey.Length &gt; <span>56</span><span>)
</span><span>throw</span> <span>new</span> ArgumentException(<span>"</span><span>UserKey is too long.</span><span>"</span><span>);
SubKey </span>= OriginPBox.Clone() <span>as</span><span> UInt32[];
SBox </span>= OriginSBox.Clone() <span>as</span><span> UInt32[,];
</span><span>for</span> (<span>int</span> i = <span>0</span>; i 18; ++<span>i) {
UInt32 temp </span>= <span>0</span><span>;
temp </span>8<span>;
temp </span>|= UserKey[(i * <span>4</span>) %<span> UserKey.Length];
temp </span>8<span>;
temp </span>|= UserKey[(i * <span>4</span> + <span>1</span>) %<span> UserKey.Length];
temp </span>8<span>;
temp </span>|= UserKey[(i * <span>4</span> + <span>2</span>) %<span> UserKey.Length];
temp </span>8<span>;
temp </span>|= UserKey[(i * <span>4</span> + <span>3</span>) %<span> UserKey.Length];
SubKey[i] </span>^=<span> temp;
}
</span><span>byte</span>[] _temp = <span>new</span> <span>byte</span>[<span>8</span><span>];
</span><span>for</span> (<span>int</span> i = <span>0</span>; i 9; ++<span>i) {
Encrypt(_temp, Endian.Little);
Buffer.BlockCopy(_temp, </span><span>0</span>, SubKey, <span>sizeof</span>(UInt32) * <span>2</span> * i, <span>8</span><span>);
}
</span></pre>
</div>
</div>
</li>
</ol></span> </p>
</div>
<div style="width:640px; height:70px; margin:auto;"></div>
<style>
.prevnext{ border-bottom: dotted 2px #cdcdcd;
overflow: hidden;
width: 624px;
margin-left: 61px;}
.prevnext p{line-height:28px; height:28px; overflow:hidden; text-overflow:ellipsis; white-space:nowrap; font-size:13px; width:364px; text-indent:6px;}
.prevnext p span{font-weight:bold;}
.prevnext p a{padding:0px !important;}
</style>
<div class="prevnext">
<p><span>上一篇:</span><a href="/index.php/essay/57230.html">Java 日期时间</a></p>
<p><span>下一篇:</span><a href="/index.php/essay/57232.html">2019-2020-2 20175303柴轩达《网络对抗技术》Exp8 Web基础</a></p>
</div>
<div class="copyright">
<div style="width:600px; float:left;">
文章来自:<a href="/index.php/" target="_blank">搜素材网</a>的<a href="/index.php/essay.html" target="_blank">编程语言</a>模块,转载请注明文章出处。<br>
文章标题:<a href="http://soscw.com/index.php/essay/57231.html" target="_blank">Navicat 密码加密算法</a><br>
文章链接:http://soscw.com/index.php/essay/57231.html </div>
</div>
<div>
<br><h3>评论</h3>
<div class="comment-area" id="comments">
<hr>
<div class="post" id="divCommentPost">亲,登录后才可以留言!</div>
<hr>
<div class="comments">
<ul class="pagination">
</ul>
</div>
</div> </div>
</div>
<div class="detail-sidebar">
<div class="essay_new">
<h3><i></i>热门文章</h3>
<ul>
<li>
<a href="/index.php/essay/104152.html">自定义WPF窗体形状</a>
</li>
<li>
<a href="/index.php/essay/102202.html">多继承c3算法与网路编程</a>
</li>
<li>
<a href="/index.php/essay/88927.html">NET Core 3.0中的WPF</a>
</li>
<li>
<a href="/index.php/essay/88314.html">导航,头部,CSS基础</a>
</li>
<li>
<a href="/index.php/essay/92954.html">&amp;#128207;Python项目打包方法</a>
</li>
<li>
<a href="/index.php/essay/88374.html">导航,头部,CSS基础</a>
</li>
<li>
<a href="/index.php/essay/42259.html">&amp;lt;3&amp;gt;Python开发——条件判断</a>
</li>
<li>
<a href="/index.php/essay/22071.html">&amp;lt;2014 04 29&amp;gt; c/c++常用库总结</a>
</li>
<li>
<a href="/index.php/essay/22174.html">&amp;#39;telnet&amp;#39; 不是内部或外部命令,也不是可运行的程序 或批处理文件。</a>
</li>
<li>
<a href="/index.php/essay/22840.html">&amp;lt;&amp;lt;&amp;lt; html编码中js和html编码不一致导致乱码</a>
</li>
</ul>
</div>
<div class="article_hot">
<h3><i></i>推荐文章</h3>
<ul>
</ul>
</div>
<div class="article_like">
<h3><i></i>最新文章</h3>
<ul>
<li>
<!--<a href="/index.php/essay/108422.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="Eclipse 发布web项目的注意点"></a>-->
<a href="/index.php/essay/108422.html">Eclipse 发布web项目的注意点</a>
</li>
<li>
<!--<a href="/index.php/essay/108421.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="实现Winform端窗体关闭后刷新html网页内容"></a>-->
<a href="/index.php/essay/108421.html">实现Winform端窗体关闭后刷新html网页内容</a>
</li>
<li>
<!--<a href="/index.php/essay/108420.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="WPF 10天修炼 - WPF布局容器"></a>-->
<a href="/index.php/essay/108420.html">WPF 10天修炼 - WPF布局容器</a>
</li>
<li>
<!--<a href="/index.php/essay/108419.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="自己写的分页器,BOOTSTRAP+JQUERY(非完全版,后续完善)"></a>-->
<a href="/index.php/essay/108419.html">自己写的分页器,BOOTSTRAP+JQUERY(非完全版,后续完善)</a>
</li>
<li>
<!--<a href="/index.php/essay/108418.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="WinSCP与Putty远程连接linux"></a>-->
<a href="/index.php/essay/108418.html">WinSCP与Putty远程连接linux</a>
</li>
<li>
<!--<a href="/index.php/essay/108417.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="C# 基础知识复习(一)"></a>-->
<a href="/index.php/essay/108417.html">C# 基础知识复习(一)</a>
</li>
<li>
<!--<a href="/index.php/essay/108416.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="jQuery对象与DOM对象转换"></a>-->
<a href="/index.php/essay/108416.html">jQuery对象与DOM对象转换</a>
</li>
<li>
<!--<a href="/index.php/essay/108415.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="windows学习记录----hello world与窗口创建"></a>-->
<a href="/index.php/essay/108415.html">windows学习记录----hello world与窗口创建</a>
</li>
<li>
<!--<a href="/index.php/essay/108414.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="Linux下利用phpize安装memcashe的php源码扩展包"></a>-->
<a href="/index.php/essay/108414.html">Linux下利用phpize安装memcashe的php源码扩展包</a>
</li>
<li>
<!--<a href="/index.php/essay/108413.html"><img src="http://soscw.com/upload/" width="150" height="100" alt="CSS3选择器 ::selection选择器"></a>-->
<a href="/index.php/essay/108413.html">CSS3选择器 ::selection选择器</a>
</li>
</ul>
</div>
<div class="article_hot">
<h3><i></i>置顶文章</h3>
<ul style="margin:-8px 0;">
</ul>
</div>
<div style="padding:20px; top:0;" id="divFixed">
</div>
</div>
</div>
</div>
<style>
.pageturn{width:1400px; height:64px; position:fixed; top:50%; left:50%; margin-left:-700px; margin-top:-32px; z-index:1;}
.pageturn>a.previouspage{width:64px; height:64px; display:block; float:left; background:url('https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/images/prevnext.png') left top no-repeat;}
.pageturn>a.previouspage:hover{background:url('https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/images/prevnext.png') left bottom no-repeat;}
.pageturn>a.nextpage{width:64px; height:64px; display:block; float:right; background:url('https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/images/prevnext.png') right top no-repeat;}
.pageturn>a.nextpage:hover{background:url('https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/images/prevnext.png') right bottom no-repeat;}
</style>
<div class="pageturn">
<a class="previouspage" href="/index.php/essay/57230.html"></a>
<a class="nextpage" href="/index.php/essay/57232.html"></a>
</div>
<div class="footer">
<div class="main">
<div class="footer_content">
<div class="footer_quick">
<a href="/index.php/portal/about/index.html" target="_blank">关于我们</a> |
<a href="/index.php/portal/about/copyright.html" target="_blank">版权声明</a> |
<a href="/index.php/portal/about/question.html" target="_blank">常见问题</a> |
<a href="/index.php/portal/about/contribute.html" target="_blank">素材投稿</a> |
<a href="/index.php/portal/about/contactUs.html" target="_blank">联系我们</a> |
<a href="/index.php/portal/about/siteMap.html" target="_blank">网站地图</a> |
</div>
<div class="footer_mail">搜素材网素材除本站原创外均由用户分享,若发现权利被侵害,请联系及时联系我们,我们会在第一时间进行处理。</div>
<div class="footer_mail">
特别说明:本站所有资源除本站原创外仅供学习与参考,请勿用于商业用途,如有侵犯您的版权请联系客服服务QQ:<a target="_blank" href="http://wpa.qq.com/msgrd?v=3&uin=2160159200&site=qq&menu=yes"><img border="0" src="http://wpa.qq.com/pa?p=2:2392512168:51" alt="点击这里给我发消息" title="点击这里给我发消息"/></a>
</a>
<script>
var _hmt = _hmt || [];
(function() {
var hm = document.createElement("script");
hm.src = "https://hm.baidu.com/hm.js?88acc0069fab2dbbe8e287a90c1e3eb5";
var s = document.getElementsByTagName("script")[0];
s.parentNode.insertBefore(hm, s);
})();
</script>
<script>
(function(){
var bp = document.createElement('script');
var curProtocol = window.location.protocol.split(':')[0];
if (curProtocol === 'https') {
bp.src = 'https://zz.bdstatic.com/linksubmit/push.js';
}
else {
bp.src = 'http://push.zhanzhang.baidu.com/push.js';
}
var s = document.getElementsByTagName("script")[0];
s.parentNode.insertBefore(bp, s);
})();
</script>
<script>(function(){
var src = (document.location.protocol == "http:") ? "http://js.passport.qihucdn.com/11.0.1.js?7a809e2fc95757dd0af994054f845937":"https://jspassport.ssl.qhimg.com/11.0.1.js?7a809e2fc95757dd0af994054f845937";
document.write('<script src="' + src + '" id="sozz"><\/script>');
})();
</script> </div>
<div class="footer_copyright">
Copyright © 2025 soscw.com 搜素材网素材网版权所有 <a href="http://www.beian.miit.gov.cn">蜀ICP备18015633号-1</a><br>
</div>
</div>
</div>
</div>
<!-- 返回顶部模块 -->
<div id="top">
<div id="izl_rmenu" class="izl-rmenu">
<a href="tencent://Message/?Uin=2392512168 &amp;websiteName=www.soscw.com=&amp;Menu=yes" class="btn btn-qq"></a>
<!--<div class="btn btn-wx">-->
<!--<div class="qrcode">-->
<!--<div class="qrcode-arrow">-->
<!--</div>-->
<!--<p>关注微信公众号</p>-->
<!--<img src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/images/weixin.jpg" alt="搜素材网素材微信公众号" width="100">-->
<!--</div>-->
<!--</div>-->
<div class="btn btn-fk" onclick="javascript:location.href=&#39;http://www.soscw.com/feedback&#39;"></div>
<div class="btn btn-top" style="display: none;"></div>
</div>
</div>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/jquery-1.8.2.min.js"></script>
<script src="/static/js/wind.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/common.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/bootstrap-collapse.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/jquery.royalslider.min.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/qrcode.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/bootstrap.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/toTop.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/login-register.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/jquery.bootstrap-autohidingnavbar.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/highlight.pack.js"></script>
<script type="text/javascript" src="https://images.dilidili.win/imgs/sourcezip/themes/fodder/public/assets/js/search.js"></script>
<script src="/static/js/frontend.js"></script>
<script src="/static/js/layer/layer.js"></script>
<script src="/static/js/ueditor/third-party/SyntaxHighlighter/shCore.js"></script>
<script src="/static/js/referrerkill.js"></script>
<script type="text/javascript">
SyntaxHighlighter.all();
</script>
<!--请在下方写此页面业务相关的脚本-->
<script>
window._bd_share_config={"common":{"bdSnsKey":{},"bdText":"","bdMini":"2","bdMiniList":false,"bdPic":"","bdStyle":"0","bdSize":"32"},"share":{}};with(document)0[(getElementsByTagName('head')[0]||body).appendChild(createElement('script')).src='http://bdimg.share.baidu.com/static/api/js/share.js?v=89860593.js?cdnversion='+~(-new Date()/36e5)];
jQuery(function() {
//遍历所有的img元素,凡是QQ和微信引用的统统放到iframe里面
jQuery("div").find("img").each(function() {
var img = jQuery(this);
var img_src = img.attr("src");
if (img_src != undefined && img_src != '') {
img_src = decodeURI(img_src);
img_src = img_src.split("?")[0];
if (img_src.indexOf("jb51") > 0 || img_src.indexOf("qlogo.cn") > 0 || img_src.indexOf("qq.com") > 0) {
var frameid = 'frameimg' + Math.random();
img.parent().append('<span id="' + frameid + '"></span>')
img.remove();
document.getElementById(frameid).innerHTML = ReferrerKiller.imageHtml(img_src);
}
}
})
})
$(function() {
// 添加浏览
$('.show').live("click",function(){
var that = $(this);
var id = that.attr("data-id");
$.ajax({
url : "/web/addview.html",
type : "post",
datatype: "json",
data : {
"id": id
},
success : function(res){
if(res.status == 1){
window.open("http://www.soscw.com" + '/demoShow/' + res['id']);
var viewNum = $(".viewNum span").text();
viewNum++;
$(".viewNum span").text(viewNum);
}else{
alert("connect error");
}
}
});
});
// 添加收藏
$('.canAddFav').live("click",function(){
var that = $(this);
var id = that.attr("data-id");
$('.canAddFav').removeClass("canAddFav");
$.ajax({
url : "/portal/Article/doLike.html",
type : "post",
datatype: "json",
data : {
"id": id
},
success : function(res){
if(res.status){
that.removeClass('addFav').addClass('unFav');
$('.unFav').addClass("canUnFav");
that.html("已收藏");
var likeNum = $(".likeNum span").html();
likeNum++;
$(".likeNum span").html(likeNum);
}else{
window.location.href = ("/user/login.html");
}
}
});
});
// 取消收藏
$('.canUnFav').live("click",function(){
var that = $(this);
var id = that.attr("data-id");
$('.canUnFav').removeClass("canUnFav");
$.ajax({
url : "/web/unfav.html",
type : "post",
datatype: "json",
data : {
"id": id
},
success : function(res){
if(res.status){
that.removeClass('unFav').addClass('addFav');
$('.addFav').addClass("canAddFav");
that.html("收藏");
var likeNum = $(".likeNum span").html();
likeNum--;
$(".likeNum span").html(likeNum);
}else{
window.open("/user/login.html");
}
}
});
});
});
</script>
</body>
</html></plaintext></enc></code></pre></li></ol></span></p></div></div>

