FreeRadius+Cisco交换机+Windows AD实现802.1X认证
2021-03-26 02:24
标签:sed init red 特殊 emc cisc 通过 认证 客户端 1.1、原理: 如上图所示,如果用户凭据已被FRIERADIUS服务器认证,则仅授予工作站的网络访问权限。否则,交换机端口将被关闭对所有的网络流量。RADIUS服务器允许与域控制器联系以进行用户身份验证。虽然交换机端口被关闭,但是工作站可以通过认证协议与RADIUS服务器通信。RADIUS服务器能够检查域控制器,如果用户存在并且密码是否正确。如果是这种情况,RADIUS服务器告诉交换机打开端口,用户将访问网络。 1.2、所需的环境 (二)、Linux服务器的安装配置 3、安装配置samba 3、配置samba服务器并重启samba服务。 4、配置/etc/krb5.conf 5、编辑/etc/nsswich.conf,在下列行末添加winbind,其他的不变 6、把改台服务器添加到域中。如果不加入到域的话,启动winbind服务会起不来出现报错。 7、启动smaba和winbind服务。 8、通过wbinfo进行账号拉取测试。wbinfo –a user%password 9、修改/var/lib/samba/winbindd_privileged权限 (三)、FreeRadius的配置 1、配置clients.conf文件,添加通信客户端。 2、配置mods-available/mschap文件。编辑/usr/local/etc/raddb/mods-available/mschap文件 3、配置mods-available/eap文件,编辑/usr/local/etc/raddb/mods-available/eap文件 4、配置/usr/local/etc/raddb/mods-enabled/ntlm_auth文件 5、编辑/etc/raddb/sites-enabled/default 和/etc/raddb/sites-enabled/inner-tunnel文件 FreeRadius+Cisco交换机+Windows AD实现802.1X认证 标签:sed init red 特殊 emc cisc 通过 认证 客户端 原文地址:http://blog.51cto.com/liqingbiao/2152850
本文档描述了如何设置FreeRadius服务器,以便对windows客户端网络用户透明的对ActiveDirectory进行身份验证。
FrReRADIUS通过基于端口的访问控制提供身份验证。只有当认证服务器验证了证书时,用户才能连接到网络。用户证书通过使用802.1x标准的特殊认证协议来验证。(FreeRADIUS offers authentication via port based access control. A user can connect to the network only if its credentials have been validated by the authentication server. User credentials are verified by using special authentication protocols which belong to the 802.1X standard.---官方文档)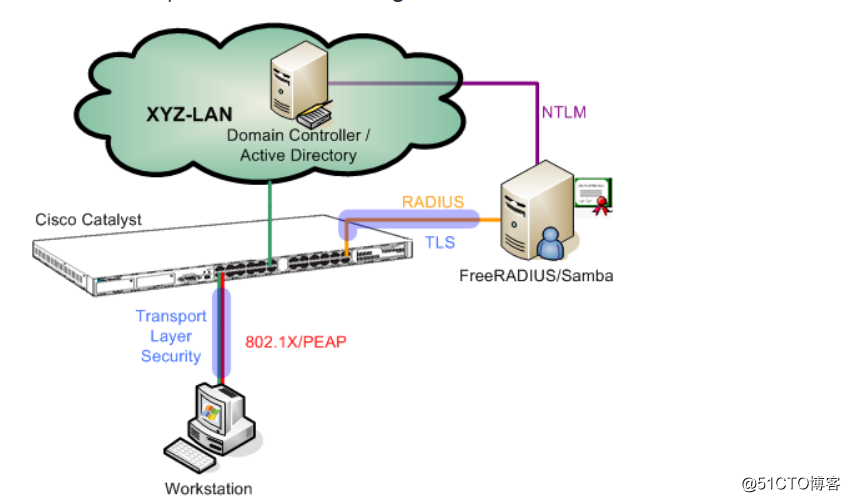
1、关闭防火墙和selinux[appuser@FreeRadius2 ~]$ sudo iptables -L -n
Chain INPUT (policy ACCEPT)
target prot opt source destination
Chain FORWARD (policy ACCEPT)
target prot opt source destination
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
[appuser@FreeRadius2 ~]$ sudo grep ‘^[a-Z]‘ /etc/selinux/config
SELINUX=disabled
SELINUXTYPE=targeted 2、编译安装freeradius[appuser@FreeRadius2 ~]# sudo xf freeradius-server-3.0.17.tar.gz
[appuser@FreeRadius2 ~]# cd freeradius-server-3.0.17
[root@FreeRadius2 freeradius-server-3.0.17]# sudo yum install libtalloc-devel -y
[root@FreeRadius2 freeradius-server-3.0.17]#yum install openssl openssl-devel
[appuser@FreeRadius2 freeradius-server-3.0.17]#sudo ./configure
[appuser@FreeRadius2 freeradius-server-3.0.17]# sudo make && make install
[root@FreeRadius2 raddb]# cp /usr/local/sbin/rc.radiusd /etc/init.d/radiused
[root@FreeRadius2 raddb]# /etc/init.d/radiused start
[root@FreeRadius2 raddb]# ps -ef|grep radiusd
root 5529 1 0 17:04 ? 00:00:00 /usr/local/sbin/radiusd
root 5537 26619 0 17:04 pts/2 00:00:00 grep --color=auto radiusd
[root@FreeRadius2 raddb]# /etc/init.d/radiused stop
Stopping FreeRADIUS: radiusd.
[root@FreeRadius2 raddb]# ps -ef|grep radiusd
[appuser@FreeRadius2 ~]$ sudo yum install samba samba-client samba-winbind krb5-server
Loaded plugins: fastestmirror
Loading mirror speeds from cached hostfile
Resolving Dependencies
--> Running transaction check
---> Package krb5-server.x86_64 0:1.15.1-19.el7 will be installed
Installed:
krb5-server.x86_64 0:1.15.1-19.el7 samba.x86_64 0:4.7.1-6.el7 samba-client.x86_64 0:4.7.1-6.el7 samba-winbind.x86_64 0:4.7.1-6.el7
Dependency Installed:
avahi-libs.x86_64 0:0.6.31-19.el7 cups-libs.x86_64 1:1.6.3-35.el7 libarchive.x86_64 0:3.1.2-10.el7_2
libevent.x86_64 0:2.0.21-4.el7 libldb.x86_64 0:1.2.2-1.el7 libsmbclient.x86_64 0:4.7.1-6.el7
libtalloc.x86_64 0:2.1.10-1.el7 libtdb.x86_64 0:1.3.15-1.el7 libtevent.x86_64 0:0.9.33-2.el7
libverto-libevent.x86_64 0:0.2.5-4.el7 libwbclient.x86_64 0:4.7.1-6.el7 pytalloc.x86_64 0:2.1.10-1.el7
samba-client-libs.x86_64 0:4.7.1-6.el7 samba-common.noarch 0:4.7.1-6.el7 samba-common-libs.x86_64 0:4.7.1-6.el7
samba-common-tools.x86_64 0:4.7.1-6.el7 samba-libs.x86_64 0:4.7.1-6.el7 samba-winbind-modules.x86_64 0:4.7.1-6.el7
words.noarch 0:3.0-22.el7
Dependency Updated:
dbus.x86_64 1:1.10.24-7.el7 dbus-libs.x86_64 1:1.10.24-7.el7 krb5-devel.x86_64 0:1.15.1-19.el7 krb5-libs.x86_64 0:1.15.1-19.el7
libkadm5.x86_64 0:1.15.1-19.el7
Complete!
一旦PAP认证测试成功,使用ActiveDirectory的站点的下一步是配置系统以对ActiveDirectory进行用户身份验证。明文密码通过ActiveDirectory不可用,因此我们必须使用SAMBA和ntlm_auth程序。在这个配置中,我们使用ActiveDirectory作为身份验证Oracle,而不是LDAP数据库。一旦Samba已经安装在您的系统上,您应该编辑SMBCONF文件,并将[Global ]部分配置为指向NT服务器,包括主机名和NT域。本文只配置samba配置文件中的[global]部分[root@FreeRadius2 raddb]# vim /etc/samba/smb.conf
[global]
workgroup = CORP ##指定域的netbios名称
security = ads ##指定samba的工作模式,和域集成
winbind use default domain = no
password server = X.X.X.X #指定定身份验证的服务器为域控
realm = CORP.BAIDU.COM #指定AD域名
[homes]
comment = Home Directories
valid users = %S, %D%w%S
browseable = No
read only = No
inherit acls = Yes
[printers]
comment = All Printers
path = /var/tmp
printable = Yes
create mask = 0600
browseable = No
[print$]
comment = Printer Drivers
path = /var/lib/samba/drivers
write list = @printadmin root
force group = @printadmin
create mask = 0664
directory mask = 0775
[root@FreeRadius2 raddb]# systemctl start smb
[root@FreeRadius2 raddb]# systemctl status smb
● smb.service - Samba SMB Daemon
Loaded: loaded (/usr/lib/systemd/system/smb.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2018-07-31 17:16:05 CST; 4s ago
Main PID: 5587 (smbd)
Status: "smbd: ready to serve connections..."
CGroup: /system.slice/smb.service
├─5587 /usr/sbin/smbd --foreground --no-process-group
├─5589 /usr/sbin/smbd --foreground --no-process-group
├─5590 /usr/sbin/smbd --foreground --no-process-group
└─5591 /usr/sbin/smbd --foreground --no-process-group
[root@FreeRadius ~]# vim /etc/krb5.conf
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
default_realm = CORP.BAIDU.COM #指定域名
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
CORP.PPDAI.COM = {
kdc = 10.128.105.170:88 #指域控为kdc服务器及端口
admin_server = 10.128.105.170:749 #指定域控的管理端口
default_domain = corp.baidu.com
}
[domain_realm]
.corp.ppdai.com = CORP.BAIDU.COM
corp.ppdai.com = CORP.BAIDU.COM
[kdc]
profile =/var/kerberos/krb5kdc/kdc.conf
[appdefaults]
pam = {
debug = false
ticket_lifetime = 36000
renew_lifetime = 36000
forwardable = true
krb4_convert = false
}[root@FreeRadius ~]# cat /etc/nsswitch.conf
passwd: files sss winbind
shadow: files sss winbind
group: files sss winbind
protocols: files sss winbind
services: files sss winbind
netgroup: files sss winbind
automount: files sss winbind[root@FreeRadius2 radiusd]# net join -U liqingbiao
Enter liqingbiao‘s password:
Using short domain name -- CORP
Joined ‘FREERADIUS2‘ to dns domain ‘corp.baidu.com‘
No DNS domain configured for freeradius2. Unable to perform DNS Update.
DNS update failed: NT_STATUS_INVALID_PARAMETER[root@FreeRadius2 radiusd]# systemctl enable winbind
[root@FreeRadius2 radiusd]# systemctl enable smb
[root@FreeRadius2 radiusd]# systemctl start winbind
[root@FreeRadius2 radiusd]# systemctl start smb
[root@FreeRadius2 radiusd]# systemctl status winbind
● winbind.service - Samba Winbind Daemon
Loaded: loaded (/usr/lib/systemd/system/winbind.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2018-07-31 17:26:30 CST; 1min 5s ago
Main PID: 5651 (winbindd)
Status: "winbindd: ready to serve connections..."
CGroup: /system.slice/winbind.service
├─5651 /usr/sbin/winbindd --foreground --no-process-group
└─5653 /usr/sbin/winbindd --foreground --no-process-group[root@FreeRadius2 appuser]# wbinfo -a it001%123456
plaintext password authentication failed
Could not authenticate user it004%Aa123456 with plaintext password
challenge/response password authentication succeeded ###成功了
[root@FreeRadius2 appuser]# ntlm_auth --request-nt-key --domain=CORP --username=it001 ###ntlm是windows 域环境下的认证方式
Password:
NT_STATUS_OK: The operation completed successfully. (0x0)[root@FreeRadius2 appuser]#usermod –G wbpriv radiusd
[root@FreeRadius2 appuser]#chown –R root.radiusd /var/lib/samba/winbindd_privileged
freeradius具体相关的配置如下:
[root@FreeRadius2 ~]# vim /usr/local/etc/raddb/clients.conf
client 172.20.19.0/24 {
secret = test
showtanme = CE-SW
}
client 172.20.66.0/24 {
secret = Aa@@123456
showtanme = CE-SW
}
client 172.20.94.0/24 {
secret = Aa@@123456
showtanme = CE-SW
}
[root@FreeRadius2 ~]# vim /usr/local/etc/raddb/mods-available/mschap with_ntdomain_hack = yes
ntlm_auth = "/usr/bin/ntlm_auth --request-nt-key --username=%{%{mschap:User-Name}:-00} --challenge=%{%{mschap:Challenge}:-00} --nt-response=%{%{mschap:NT-Response}:-00} --domain=%{%{mschap:NT-Domain}:-CORP.BAIDU.COM}"[root@FreeRadius2 ~]# vim /usr/local/etc/raddb/mods-available/eap
default_eap_type = peap.
random_file = /dev/urandom[root@FreeRadius2 ~]# vim /usr/local/etc/raddb/mods-enabled/ntlm_auth
exec ntlm_auth {
wait = yes
program = "/usr/bin/ntlm_auth --request-nt-key --domain=CORP.PPDAI.COM --username=%{mschap:User-Name} --password=%{User-Password}"authenticate { ... ntlm_auth ...}
上一篇:Windows下编译jcef
文章标题:FreeRadius+Cisco交换机+Windows AD实现802.1X认证
文章链接:http://soscw.com/index.php/essay/68020.html