树莓派/Debian Apache2 配置自建 CA 实现 HTTPS(SSL) 服务
2021-04-07 08:27
标签:info 两种方法 登录 ide internet hang for starting sub 前文 树莓派/Debian Apache2 实现 HTTPS(SSL) 服务 提到,Apache2 实现 HTTPS(SSL) 服务有两种方法以及之间的区别,这里讲述如何通过 OpenSSL 自建 CA 来 自签名证书 和 颁发 SSL 证书 实现 HTTPS(SSL) 服务。 这一步必做 。 以 root 权限执行命令: 这时应显示: 在此初始工作环境中,子目录的重要性及其内容如下: 成功显示: 过程中,提示需要你输入该根证书相关信息,自行更改: 成功显示: 成功显示: 过程中,提示需要你输入该根证书相关信息,自行更改: 创建配置文件 openssl.cnf 参考如下: 需要将 Server 监听的地址写入证书中,如果访问时地址与证书中地址不一致将不能通过证书认证。 执行命令生成 Server 证书 成功显示: 使用 这一步必做 。 以 root 权限执行命令: 这时应显示: 以 root 权限启用SSL模块: 如果执行成功显示: 它最后提醒你执行一条重启命令: 这里要以 root 权限执行这条命令,否则报错。 注意:这里重启了 Apache2。 这一步必做,和前两步的 “停止 Apache2 服务” 起到同样的效果 。 以 root 权限执行命令: 这时应显示: 以 root 权限执行命令: 正确返回结果: 它提醒执行 这时 启动 Apache2 服务 : 启动成功显示: 启动 Apache2 服务成功后,加载 SSL 配置文件 default-ssl.conf 成功无显示。 加载完成了,修改其配置。 编辑监听端口配置文件 一般显示: 添加监听端口 443 将示例中第 5 行 编辑 SSL 配置文件 default-ssl.conf 如果忽略注释会显示: 添加 这里的主机名填写为: 按 OpenSSL 文档操作时文件 exampleserver.cnf 中的 修改加载 SSL 证书位置,例: 输入命令重启 Apache2 服务 成功会显示: 配benz置成功。 树莓派/Debian Apache2 配置自建 CA 实现 HTTPS(SSL) 服务 标签:info 两种方法 登录 ide internet hang for starting sub 原文地址:https://www.cnblogs.com/Yogile/p/12487790.html树莓派/Debian Apache2 配置自建 CA 实现 HTTPS(SSL) 服务
一、前言
1. 下载 Apache2
sudo apt-get install apache22. 停止 Apache2 服务
sudo /etc/init.d/apache2 stop[ ok ] Stopping apache2 (via systemctl): apache2.service.二、自建 CA
1. 创建工作环境
cd /etc/apache2/ && sudo mkdir -p ownSSL/CA && sudo mkdir ownSSL/Server && cd /etc/apache2/
/etc/apache2/ownSSL/CA : 包含CA私匙、CA 证书请求、CA根证书
/etc/apache2/ownSSL/Server : 包含Server私匙、Server证书请求、Server证书1. 生成 CA 私匙
sudo openssl genrsa -out CA/CA_private.key 2048Generating RSA private key, 2048 bit long modulus (2 primes)
................+++++
...................................................+++++
e is 65537 (0x010001)2. 生成 CA 证书请求
sudo openssl req -new -key CA/CA_private.key -out CA/CA_request.csrYou are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BeiJing
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Yogile
Organizational Unit Name (eg, section) []:Yogile
Common Name (e.g. server FQDN or YOUR name) []:Yogile
Email Address []:example@mail.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:opensslca
An optional company name []:Yogile
3. 生成 CA 根证书
sudo openssl x509 -req -in CA/CA_request.csr -extensions v3_ca -signkey CA/CA_private.key -out CA/CA_root.crt
Signature ok
subject=C = CN, ST = BeiJing, L = BJ, O = Yogile, OU = Yogile, CN = Yogile, emailAddress = example@mail.com
Getting Private key
三、自建 Server 端证书
1. 生成 Server 私匙
sudo openssl genrsa -out Server/Server_private.key 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
............+++++
.......................+++++
e is 65537 (0x010001)
2. 生成 Server 证书请求
sudo openssl req -new -key Server/Server_private.key -out Server/Server_request.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:CN
State or Province Name (full name) [Some-State]:BeiJing
Locality Name (eg, city) []:BJ
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Yogile
Organizational Unit Name (eg, section) []:Yogile
Common Name (e.g. server FQDN or YOUR name) []:Yogile
Email Address []:example@mail.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:example@mail.com
An optional company name []:Yogile
3. 生成 Server 证书
sudo vim openssl.cnf
[req]
distinguished_name = req_distinguished_name
req_extensions = v3_req
[req_distinguished_name]
countryName = CN
countryName_default = CN
stateOrProvinceName = BJ
stateOrProvinceName_default = BeiJing
localityName = BJ
localityName_default = BeiJing
organizationalUnitName = Yogile
organizationalUnitName_default = Domain Control Validated
commonName = Internet Widgits Ltd
commonName_max = 64
[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names
[alt_names]
# 注意这个IP.1的设置,IP地址需要和你的服务器的监听地址一样 DNS为server网址
IP.1 = 192.168.0.129
DNS.1 = www.example.com
sudo openssl x509 -days 365 -req -in Server/Server_request.csr -extensions v3_req -CAkey CA/CA_private.key -CA CA/CA_root.crt -CAcreateserial -out Server/Server_root.crt -extfile openssl.cnf
Signature ok
subject=C = CN, ST = BeiJing, L = BJ, O = Yogile, OU = Yogile, CN = Yogile, emailAddress = example@mail.com
Getting CA Private Key四、检查目录结构,确定无误
tree 命令检查环境良好,配置无误:yogile@debyogile:/etc/apache2/ownSSL$ tree
.
├── CA
│?? ├── CA_private.key
│?? ├── CA_request.csr
│?? ├── CA_root.crt
│?? └── CA_root.srl
├── openssl.cnf
└── Server
├── Server_private.key
├── Server_request.csr
└── Server_root.crt
2 directories, 8 files五、Apache2 SSL 证书加载
1. 停止 Apache2 服务
sudo /etc/init.d/apache2 stop
[ ok ] Stopping apache2 (via systemctl): apache2.service.
2. 启用SSL模块
sudo a2enmod ssl
Considering dependency setenvif for ssl:
Module setenvif already enabled
Considering dependency mime for ssl:
Module mime already enabled
Considering dependency socache_shmcb for ssl:
Enabling module socache_shmcb.
Enabling module ssl.
See /usr/share/doc/apache2/README.Debian.gz on how to configure SSL and create self-signed certificates.
To activate the new configuration, you need to run:
systemctl restart apache2
sudo /etc/init.d/apache2 restart
3. 停止 Apache2 服务
sudo /etc/init.d/apache2 stop
[ ok ] Stopping apache2 (via systemctl): apache2.service.
4. 加载 SSL 配置文件 default-ssl.conf
sudo a2ensite default-ssl
yogile@debyogile:/etc/apache2# sudo a2ensite default-ssl
a2ensite default-sslEnabling site default-ssl.
To activate the new configuration, you need to run:
systemctl reload apache2
systemctl reload apache2 ,先不管它,进行下一步 启动 Apache2 服务 。sudo /etc/init.d/apache2 start
[ ok ] Starting apache2 (via systemctl): apache2.service.
sudo systemctl reload apache2
四、Apache2 SSL 证书配置
1. 添加监听端口
sudo vim /etc/apache2/ports.conf
# If you just change the port or add more ports here, you will likely also
# have to change the VirtualHost statement in
# /etc/apache2/sites-enabled/000-default.conf
Listen 80
Listen 80 修改成 Listen 80 443 :# If you just change the port or add more ports here, you will likely also
# have to change the VirtualHost statement in
#/etc/apache2/sites-enabled/000-default.conf
Listen 80 443
:wq 保存退出2. 修改 SSL 配置文件 default-ssl.conf
sudo vim /etc/apache2/sites-enabled/default-ssl.conf
ServerName ,例:ServerAdmin webmaster@localhost
ServerName yogile.icu
DocumentRoot /var/www/html
DNS.0 :[ alt_names ]
DNS.0 = yogile.icu
DNS.1 = www.yogile.icu
SSLCertificateFile /etc/apache2/ownSSL/Server/Server_root.crt
SSLCertificateKeyFile /etc/apache2/ownSSL/Server/Server_private.key
:wq 保存退出3. 重启 Apache2 服务
sudo /etc/init.d/apache2 restart
[ ok ] Restarting apache2 (via systemctl): apache2.service.
五、网页登录测试
1. 在浏览器中输入域名、公网 IP 或私网 IP
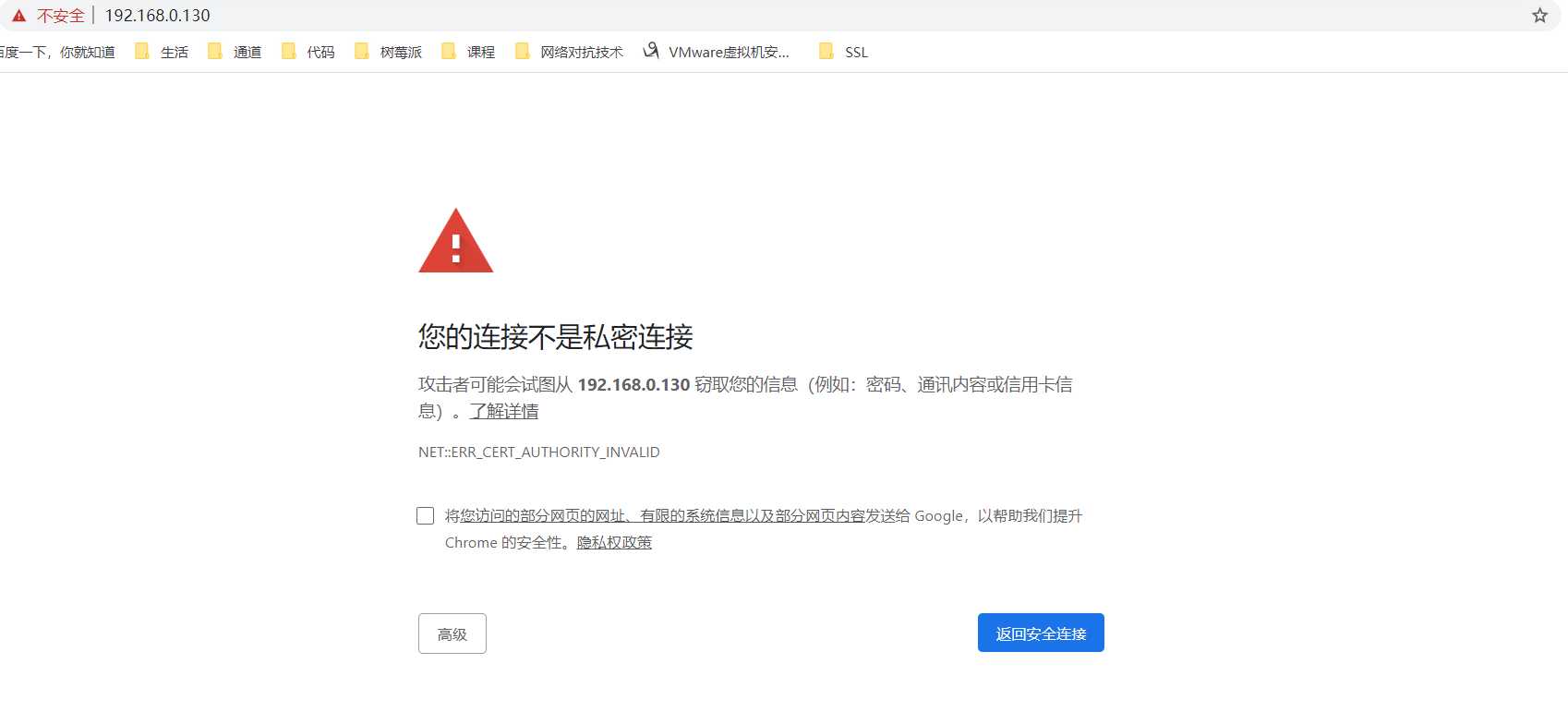
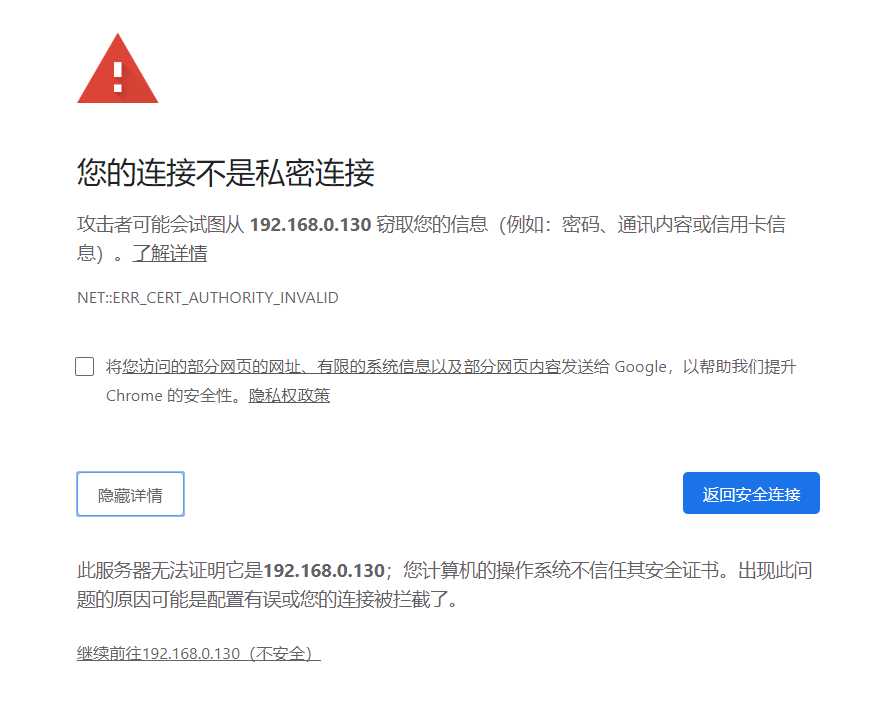
2. 点击
“高级” -> 继续前往(不安全)
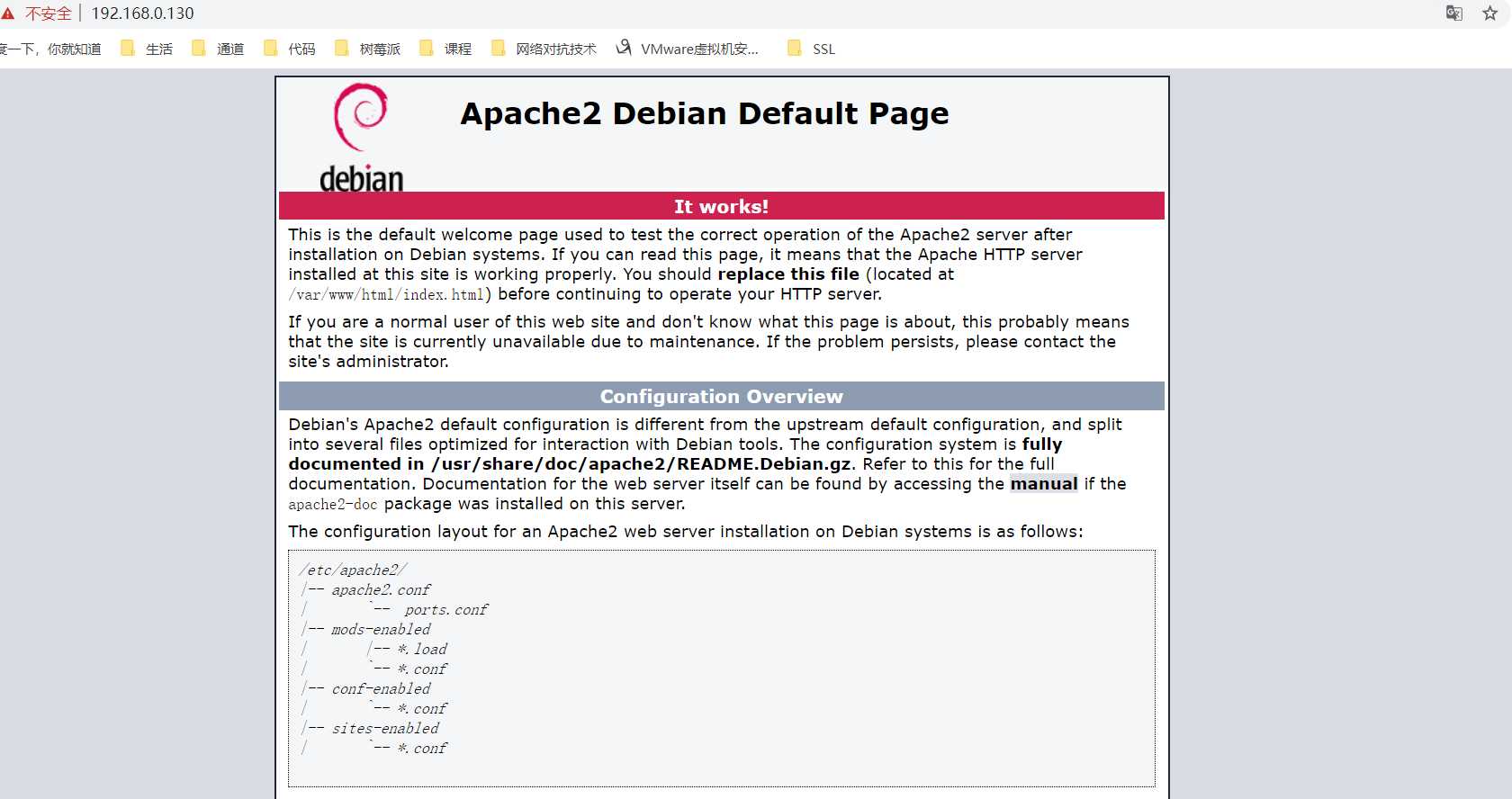
3. HTTPS(SSL) 配置成功
文章标题:树莓派/Debian Apache2 配置自建 CA 实现 HTTPS(SSL) 服务
文章链接:http://soscw.com/index.php/essay/72323.html