11 . KubernetesRBAC认证及ServiceAccount、Dashboard
2021-01-26 08:14
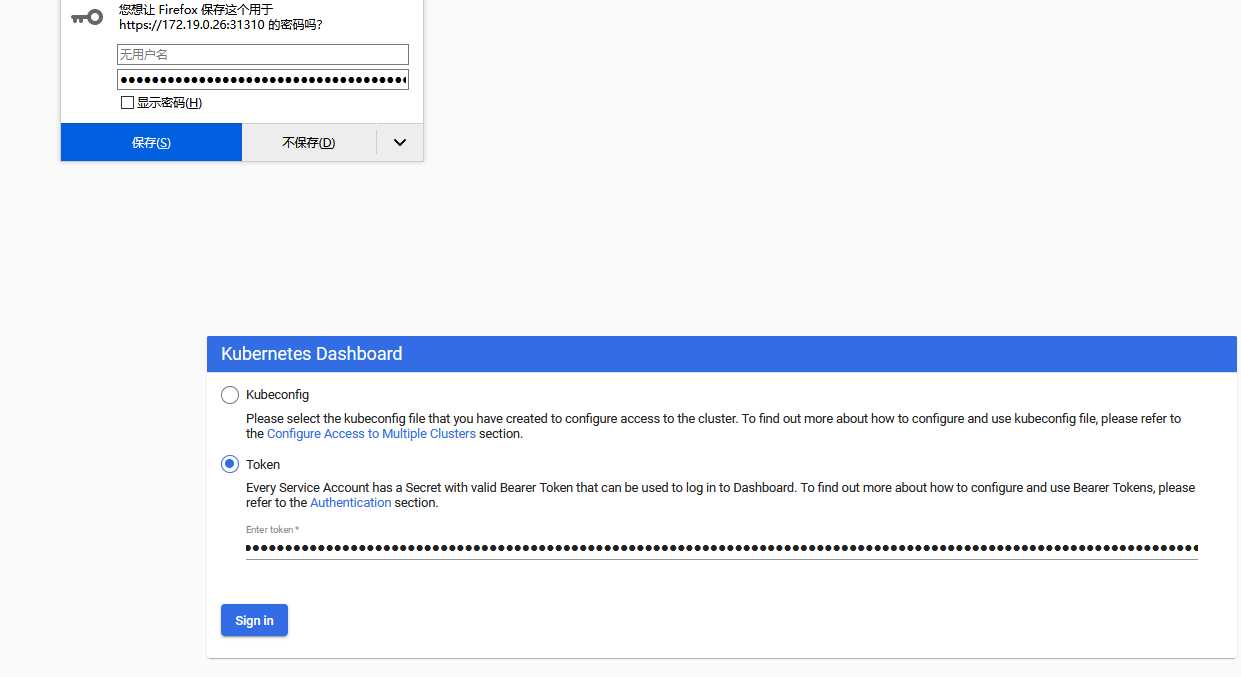
标签:技术 谷歌 issue 指定 int resource creat python 登录 RBAC是基于角色的访问控制 (Role-Based Access Control) 在RBAC中,权限与角色相关联。Kubernetes 基于角色的访问控制使用rbac.authorization.k8s.io API组来实现权限控制,RBAC允许管理员通过Kubernetes API动态的配置权限策略。如果需要开启RBAC授权需要在apiserver组件中指定--authorization-mode=Node,RBAC 什么是service account? 顾名思义,相对于user account(比如:kubectl访问APIServer时用的就是user account),service account就是Pod中的Process用于访问Kubernetes API的account,它为Pod中的Process提供了一种身份标识。相比于user account的全局性权限,service account更适合一些轻量级的task,更聚焦于授权给某些特定Pod中的Process所使用。 Dashboard 是基于网页的 Kubernetes 用户界面。您可以使用 Dashboard 将容器应用部署到 Kubernetes 集群中,也可以对容器应用排错,还能管理集群本身及其附属资源。您可以使用 Dashboard 获取运行在集群中的应用的概览信息,也可以创建或者修改 Kubernetes 资源(如 Deployment,Job,DaemonSet 等等)。例如,您可以对 Deployment 实现弹性伸缩、发起滚动升级、重启 Pod 或者使用向导创建新的应用。 APIServer是整个访问请求进入的网关接口,认证用于实现身份识别,授权用于权限检查. K8s有两类账号 创建Serviceaccount 我们正常敲kubectl get pods时候有哪些认证 创建自己的一个用户 创建一个上下文可以访问集群 我们切换到youmen用户尝试一下 自己创建一个cluster集群 RBAC授权 role: rolebinding: 如果使用rolebinding绑定到clusterrole上,表示绑定的用户只能用于当前namespace的权限 查看并验证绑定授权用户 创建clusterrole,可以访问全部的namespace 验证clusterrolebinding flannel控制 Kubernetes集群的管理方式: 命令式: create,run,expose,delete,.. 命令式配置文件: create -f /PATH/TO/RESOURCE_CONFGURATION_FILE ,delete -f ,replace -f 声明式配置文件: apply -f,patch 部署 将Service改为NodePort 认证 config: (把ServiceAccount的token封装为kubeconfig文件) 因为其他浏览器打不开是因为证书过期,我们可以解决证书过期问题 API Server访问Dashboard(推荐) 使用Token登录 在创建一个账号,拥有对default名称空间的权限 配置文件认证 11 . KubernetesRBAC认证及ServiceAccount、Dashboard 标签:技术 谷歌 issue 指定 int resource creat python 登录 原文地址:https://www.cnblogs.com/you-men/p/13232886.html简介
Kubernetes RBAC角色权限控制
ServiceAccount
Dashboard
Kubernetes RBAC
# 一种是用户账号user,一般是现实中人使用账号
# 第二种是service账号,服务账号,Pod运行在K8s集群上,想访问K8s集群APIServer里面要用到的认证信息,账号密码等.
API
Request path
http://localhost:6443/apis/apps/v1/namespaces/defaults/myapp-deplyoy/
HTTP requests verb:
get,post,put,delete
API requets verb:
get,list,create,update,patch,watch,proxy,redirect,delete,deletecollection
Resource:
Subresource:
Namespace
API group
# 快速创建一个yaml框架
kubectl create serviceaccount mysa -o yaml --dry-run > serviceaccount.yaml
kubectl get pods nginx-deployment-5dcb7cf7db-mjlsq -o yaml --export
kubectl create serviceaccount admin
kubectl get sa
NAME SECRETS AGE
admin 1 4s
default 1 4d8h
mysa 1 3m45s
# 这些认证不一定等于授权
kubectl get secret
NAME TYPE DATA AGE
admin-token-9sxbn kubernetes.io/service-account-token 3 35s
default-token-kr5s2 kubernetes.io/service-account-token 3 4d8h
mysa-token-rg974 kubernetes.io/service-account-token 3 4m16s
cat pod-demo1.yaml
apiVersion: v1
kind: Pod
metadata:
name: pod-sa-demo
namespace: default
labels:
app: myapp
tier: frontend
annotations:
youmen.com/create-by: "youmen admin"
spec:
containers:
- name: myapp
image: ikubernetes/myapp:v1
ports:
- name: http
containerPort: 80
kubectl describe pod pod-sa-demo |grep token
/var/run/secrets/kubernetes.io/serviceaccount from admin-token-9sxbn (ro)
admin-token-9sxbn:
SecretName: admin-token-9sxbn
Serviceaccount认证
kubectl config view
apiVersion: v1
clusters: # 集群列表
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.78.7:6443
name: kubernetes
contexts: # 上下文列表
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users: # 用户列表
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
cd /etc/kubernetes/pki/
# 创建私钥
(umask 077;openssl genrsa -out youmen.key 2048)
openssl req -new -key youmen.key -out youmen.csr -subj "/CN=youmen"
openssl x509 -req -in youmen.csr -CA ./ca.crt \
-CAkey ./ca.key -CAcreateserial -out youmen.crt -days 365
openssl x509 -in youmen.crt -text -noout
Certificate:
Data:
Version: 1 (0x0)
Serial Number:
e6:1c:db:0b:a5:ca:01:db
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=kubernetes
Validity
Not Before: Dec 25 15:35:54 2019 GMT
Not After : Dec 24 15:35:54 2020 GMT
Subject: CN=youmen
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
kubectl config set-credentials youmen --client-certificate=./youmen.crt --client-key=./youmen.key --embed-certs=true
kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.78.7:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: youmen
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
kubectl config set-context youmen@kubernetes --cluster=kubernetes --user=youmen
Context "youmen@kubernetes" created.
[root@master pki]# kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.78.7:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: youmen
name: youmen@kubernetes
current-context: kubernetes-admin@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: youmen
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
kubectl config use-context youmen@kubernetes
Switched to context "youmen@kubernetes".
kubectl get pods
Error from server (Forbidden): pods is forbidden: User "youmen" cannot list resource "pods" in API group "" in the namespace "default"
kubectl config set-cluster mycluster \
--kubeconfig=/tmp/test.conf \
--server="https://172.19.0.41:6443" \
--certificate-authority=/etc/kubernetes/pki/ca.crt \
--embed-certs=true
kubectl config view --kubeconfig=/tmp/test.conf
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.19.0.41:6443
name: mycluster
contexts: null
current-context: ""
kind: Config
preferences: {}
users: null
之前我们切换用户get pods时候发现报错,还未赋予权限
k8s授权请求是http的请求/apis/[GROUP]/[VERSION]/namespace/[NAMESPACE_NAME]/[KIND]/[OBJECT_ID]
k8s授权方式分为:
serviceccount和自己签证ca证书的账号,及签证ca的用户组(group)上(授权给这个组的权限)# 1. 允许的操作,如get,list等
# 2. 允许操作的对象,如pod,svc等
# 将那个用户绑定到那个role或clusterrrole上
# clusterrole: (集群角色)
# clusterolebinding:(绑定到集群)
kubectl create role pods-reader --verb=get,list,watch --resource=pods --dry-run -o yaml>role-demo.yaml
cat role-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
creationTimestamp: null
name: pods-reader
namespace: default
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
kubectl get role
NAME AGE
pods-reader 48s
kubectl describe role pods-reader
Name: pods-reader
Labels: kubectl describe rolebinding youmen-read-pods
Name: youmen-read-pods
Labels:
kubectl create clusterrole cluster-reader --verb=get,list,watch --resource=pods -o yaml --dry-run \
> clusterrole-demo.yaml
useradd k8s
cp -rp .kube/ /home/k8s/
chown -R k8s:k8s /home/k8s/
su - k8s
kubectl config view
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://172.19.0.26:6443
name: kubernetes
contexts:
- context:
cluster: kubernetes
user: kubernetes-admin
name: kubernetes-admin@kubernetes
- context:
cluster: kubernetes
user: youmen
name: youmen@kubernetes
current-context: youmen@kubernetes
kind: Config
preferences: {}
users:
- name: kubernetes-admin
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
- name: youmen
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
cat cluterrole-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: cluster-reader
rules:
- apiGroups:
- ""
resources:
- pods
verbs:
- get
- list
- watch
kubectl apply -f cluterrole-demo.yaml
# 我们将之前的role删掉,然后会发现立马就没权限查看Pod了
kubectl delete rolebinding youmen-read-pods
kubectl get pods
Error from server (Forbidden): pods is forbidden: User "youmen" cannot list resource "pods" in API group "" in the namespace "default"
# 接下来我们使用clusterrolebinding更大的权限**
kubectl create clusterrolebinding youmen-read-all-pods --clusterrole=cluster-reader --user=youmen
kubectl create clusterrolebinding youmen-read-all-pods --clusterrole=cluster-reader --user=youmen --dry-run -o yaml \> clusterrolebinding-demo.yaml
vim clusterrolebinding-demo.yaml
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
creationTimestamp: null
name: youmen-read-all-pods
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: youmen
kubectl get clusterrolebinding |grep youmen
youmen-read-all-pods 2m18s
kubectl describe clusterrolebinding youmen-read-all-pods
Name: youmen-read-all-pods
Labels: kubectl get pods -n kube-system
NAME READY STATUS RESTARTS AGE
coredns-6955765f44-5jlbk 1/1 Running 1 7d17h
coredns-6955765f44-xnr7f 1/1 Running 1 7d17h
etcd-master 1/1 Running 1 7d17h
kube-apiserver-master 1/1 Running 1 7d17h
kubectl delete clusterrolebinding youmen-read-all-pods
# 我们将它删除,在创建一个新的clusterrolebinding
kubectl create rolebinding youmen-read-pods \
--clusterrole=cluster-reader \
--user=youmen --dry-run -o yaml > rolebinding-clusterrole.demo.yaml
cat rolebinding-clusterrole.demo.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
creationTimestamp: null
name: youmen-read-pods
namespace: default
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-reader
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: youmen
kubectl apply -f rolebinding-clusterrole.demo.yaml
kubectl describe rolebinding youmen-read-pods
Name: youmen-read-pods
Labels: kubectl get pods -n kube-system kube-flannel-ds-amd64-jw4xk -o yaml
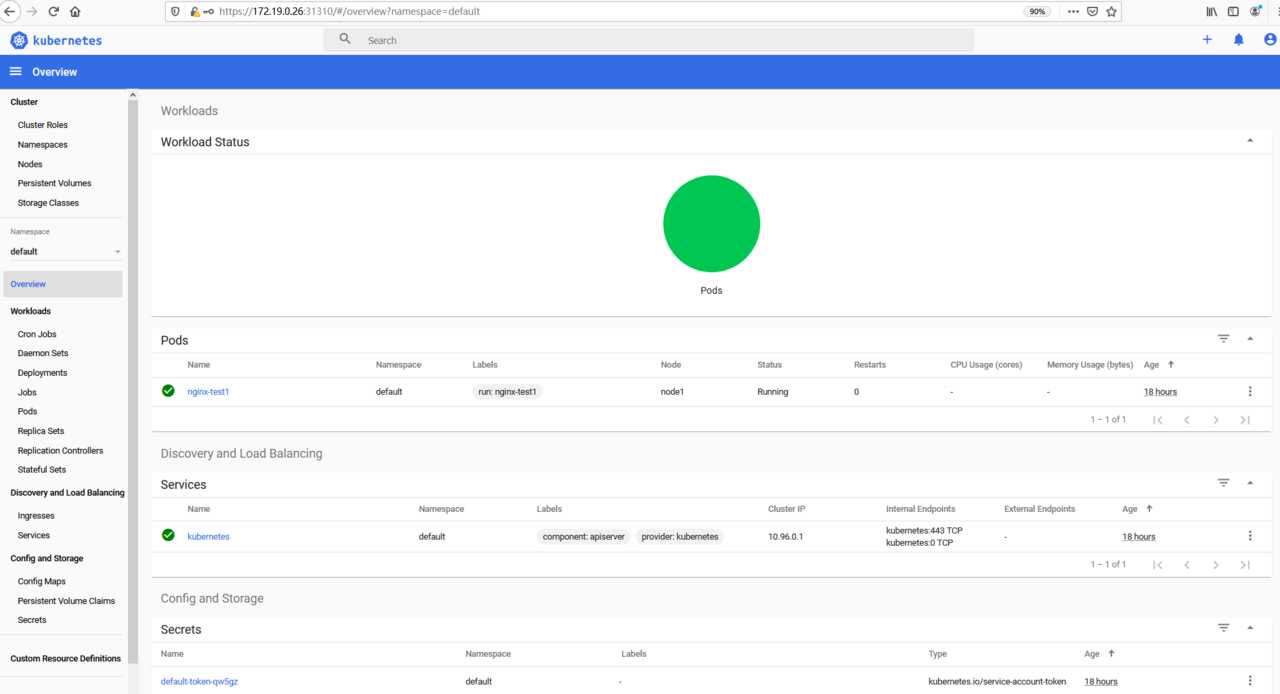
Dashboard
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0-beta8/aio/deploy/recommended.yaml
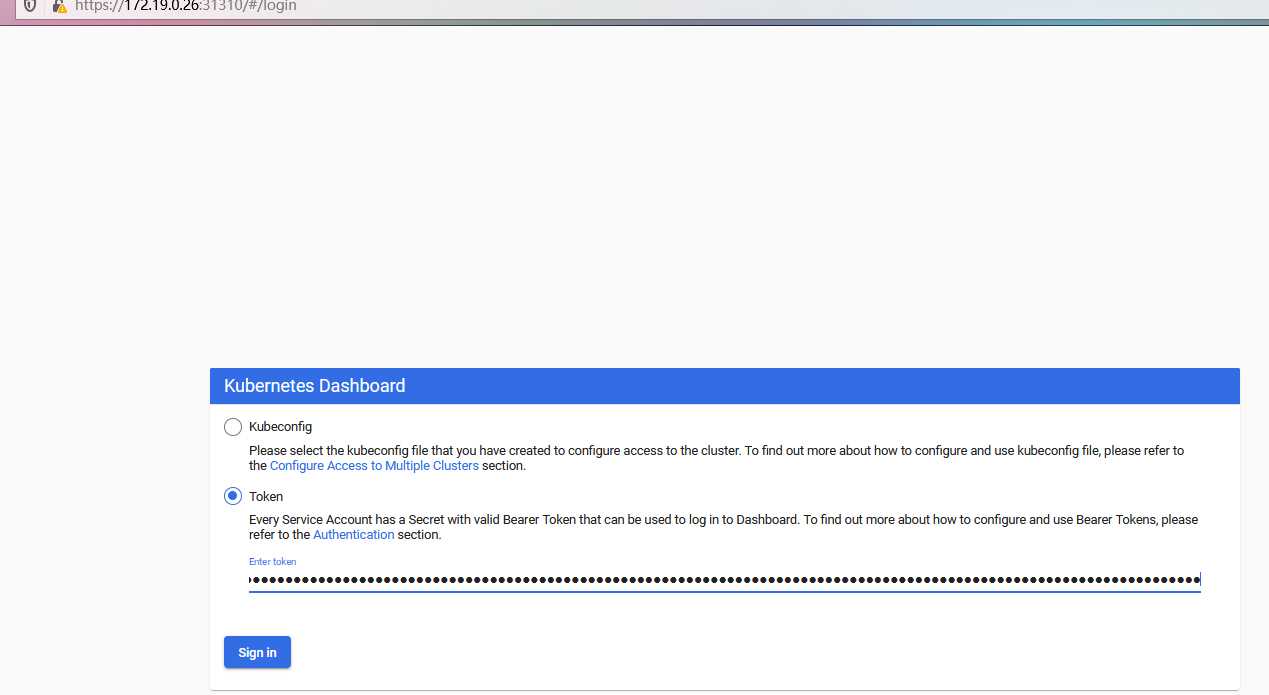
token:
1. 创建ServiceAccount,根据其管理目标,使用rolebinding或clusterrolebinding绑定至合理role或clusterrole;
2.kubectl get secret |awk ‘/^ServiceAccount/{print $1}‘
DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-mnpph -o jsonpath={.data.token} |base64 -d )
3. 生成kubeconfig文件
kubectl config set-cluster --kubeconfig=/PATH/TO/SOMEFILE
kubectl config set-credentials NAME --token=$KUBE_TOKEN --kubeconfig=/PATH/TO/SOMEFILE
kubectl config set-context
kubectl config use-context# 我们通过打补丁实现NodePort外部访问k8sUI (不建议)
kubectl patch -n kubernetes-dashboard svc kubernetes-dashboard -p ‘{"spec":{"type":"NodePort"}}‘
service/kubernetes-dashboard patched
[root@master dashboard]# kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.96.191.177 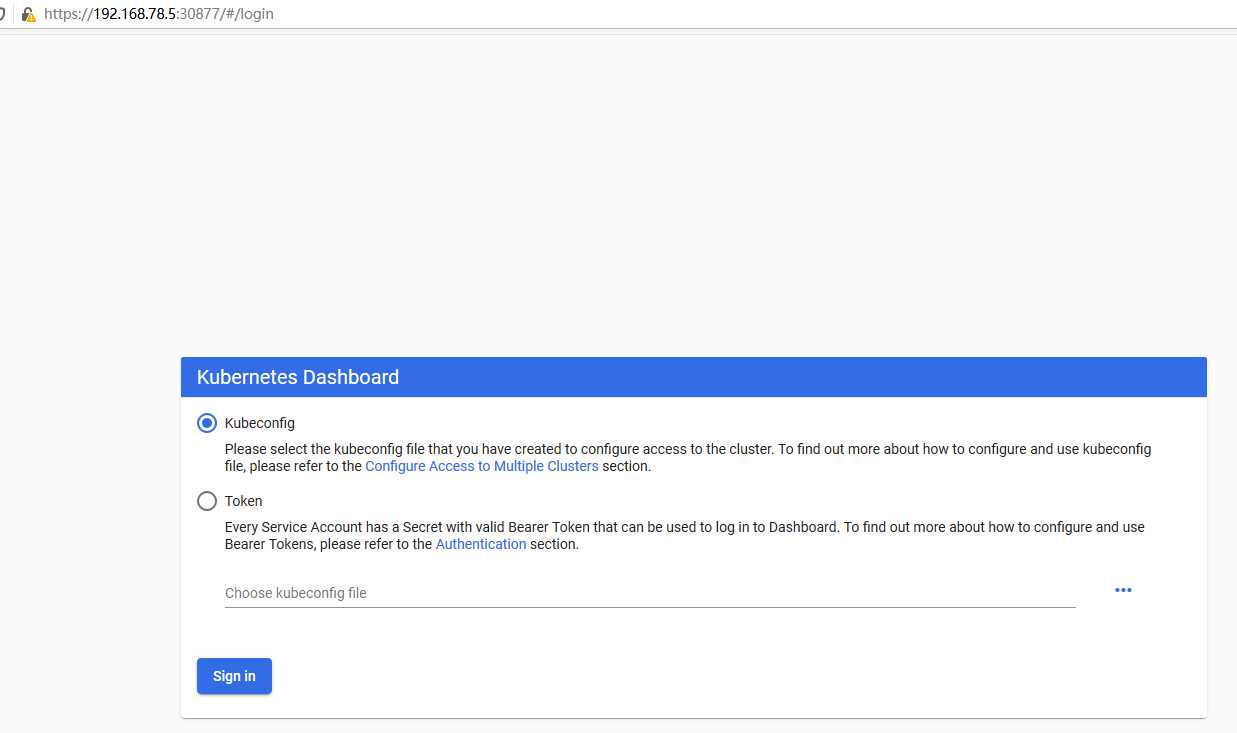
# 首先需要生成证书
# 如果Kubernetes API服务器是公开的,并可以从外部访问,我们可以直接使用API Server的方式来访问.
# https://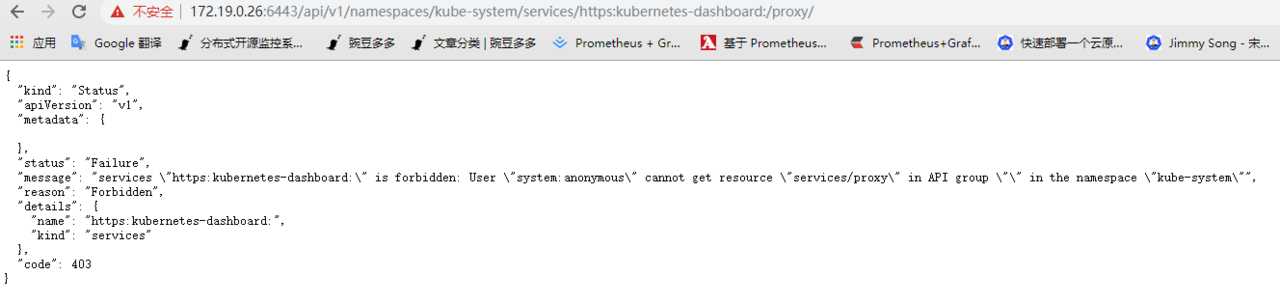
# 1. 首先找到kubectl命令的配置文件,默认情况下为/etc/kubernetes/admin.conf
# 2. 然后我们使用client-certificate-data和client-key-data生成一个*p12*文件,可使用下列命令:
# 生成client-certificate-data
grep ‘client-certificate-data‘ ~/.kube/config | head -n 1 | awk ‘{print $2}‘ | base64 -d >> kubecfg.crt
# 生成client-key-data
grep ‘client-key-data‘ ~/.kube/config | head -n 1 | awk ‘{print $2}‘ | base64 -d >> kubecfg.key
# 生成p12
openssl pkcs12 -export -clcerts -inkey kubecfg.key -in kubecfg.crt -out kubecfg.p12 -name "kubernetes-client"
ls
kubecfg.crt kubecfg.key kubecfg.p12
# 最后导入上面生成的p12文件,重新打开浏览器,显示如下
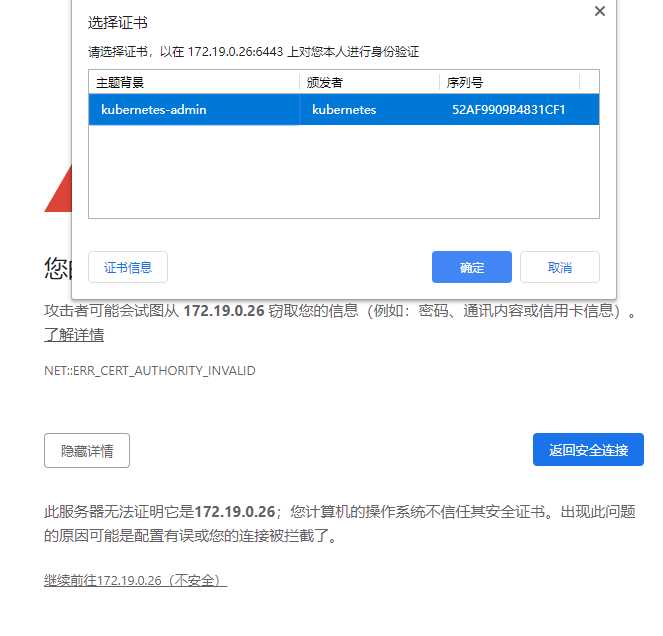
kubectl create serviceaccount dashboard-admin -n kube-system
kubectl create clusterrolebinding dashboard-cluster-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
kubectl get secret -n kube-system |grep dashboard
dashboard-admin-token-drb8d kubernetes.io/service-account-token 3 2m43s
dashboard-cert Opaque 2 21m
kubectl describe secret dashboard-admin-token-drb8d -n kube-system
kubectl create serviceaccount def-ns-admin -n default
kubectl create rolebinding def-ns-admin --clusterrole=admin --serviceaccount=default:def-ns-admin
kubectl get secret
NAME TYPE DATA AGE
def-ns-admin-token-mnpph kubernetes.io/service-account-token 3 2m29s
default-token-qw5gz kubernetes.io/service-account-token 3 18h
[root@master pki]# kubectl describe secret def-ns-admin-token-mnpph
kubectl config set-cluster kubernetes --certificate-authority=./ca.crt --server="https://172.19.0.26:6443" --embed-certs=true --kubeconfig=/root/def-ns-admin.conf
Cluster "kubernetes" set.
[root@master pki]# kubectl config view --kubeconfig=/roo/def-ns-admin.conf
apiVersion: v1
clusters: null
contexts: null
current-context: ""
kind: Config
preferences: {}
users: null
kubectl get secret def-ns-admin-token-mnpph -o json
DEF_NS_ADMIN_TOKEN=$(kubectl get secret def-ns-admin-token-mnpph -o jsonpath={.data.token} |base64 -d )
kubectl config set-credentials def-ns-admin --token=$DEF_NS_ADMIN_TOKEN --kubeconfig=/root/def-ns-admin.conf
kubectl config view --kubeconfig=/root/def-ns-admin.conf
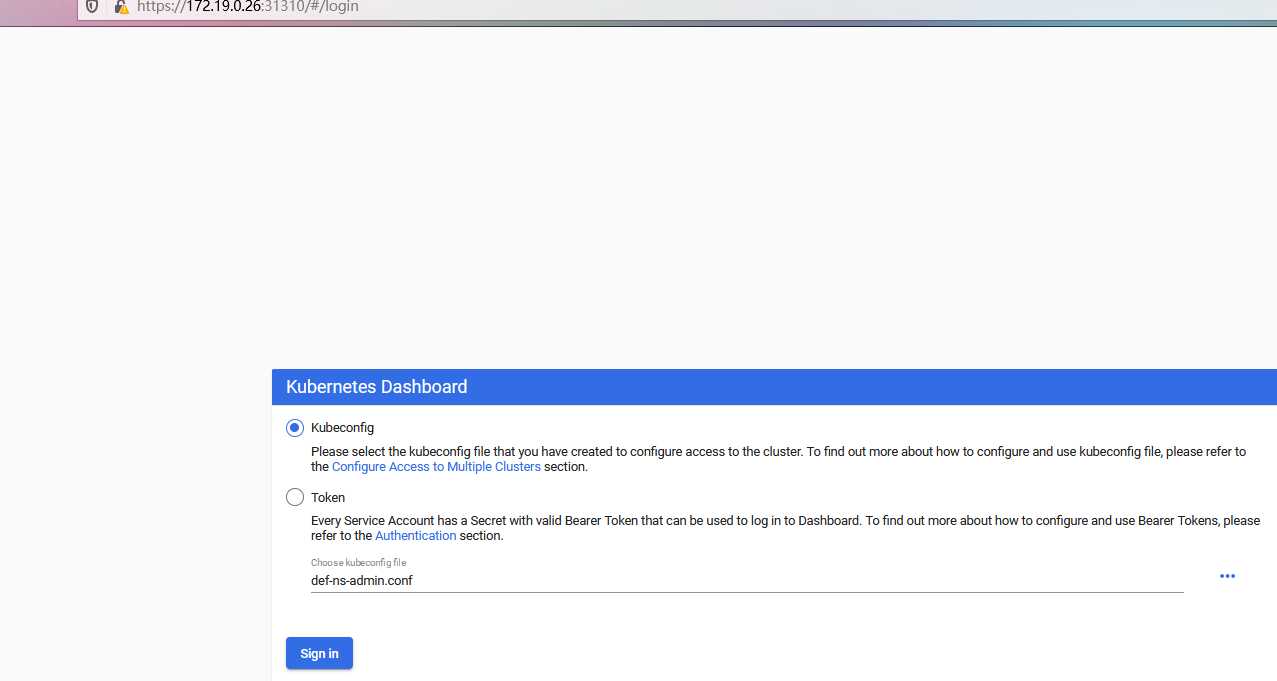
kubectl config set-context def-ns-admin@kubernetes --cluster=kubernetes --user=def-ns-admin --kubeconfig=/root/def-ns-admin.conf
kubectl config use-context def-ns-admin@kubernetes --kubeconfig=/root/def-ns-admin.conf
kubectl config view --kubeconfig=/root/def-ns-admin.conf
# 将此文件上传到电脑目录上.
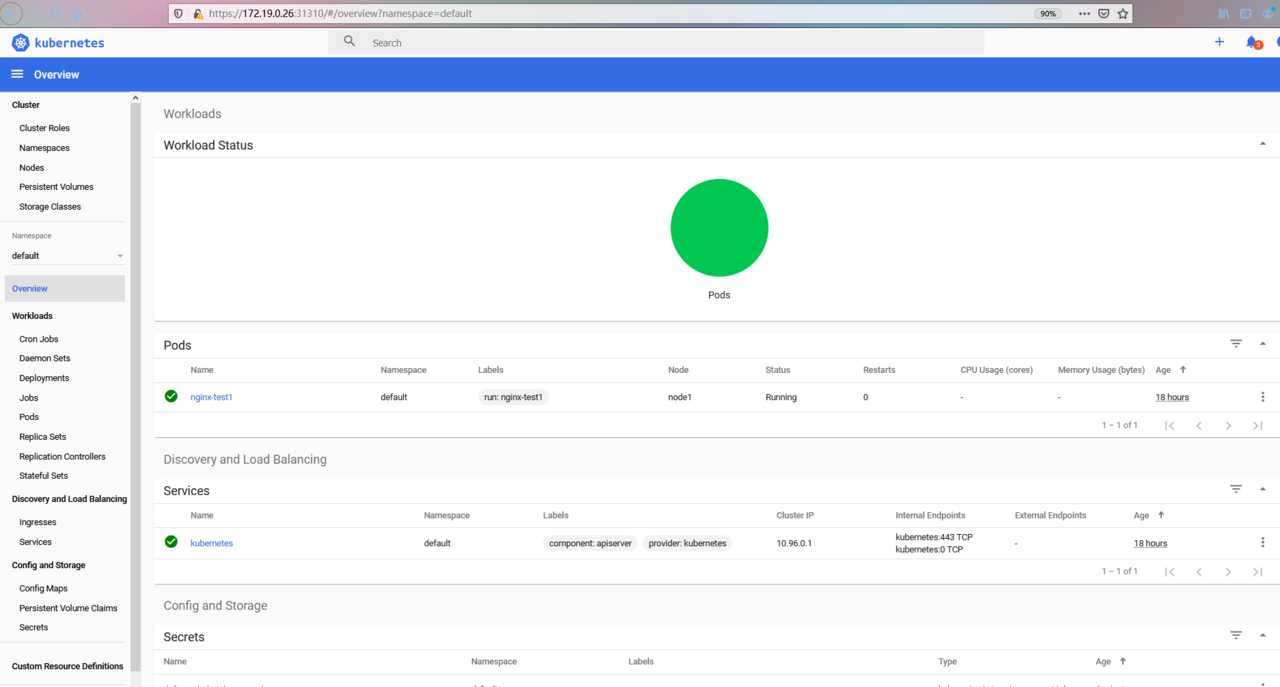
文章标题:11 . KubernetesRBAC认证及ServiceAccount、Dashboard
文章链接:http://soscw.com/index.php/essay/47188.html